However, it’s illegal if you venture into the dark web to commit unlawful actions such as downloading child porn, buying fake documents, drugs, credits card, and more. Fraudulent activities on the dark web include phishing scams, fake identity sales, and the sale of fake products. Counterfeiting businesses create fake versions of popular products and sell them on the dark web.

It is a specific Debian-based version of Linux software that leaves no traces of the user activity or the operating system on the computer. It uses the Tor network because it is a popular network that helps to circumvent censorship and online surveillance. Impreza Hosting is a web hosting service that distinguishes itself by emphasizing privacy and security. From its inception, Ahmia has been committed to ethical principles, filtering out content related to child pornography and maintaining a blacklist to mitigate abusive services. This commitment underlines the search engine’s dedication to providing a safe and constructive environment for dark web exploration.
Dark Web Tools & Services
This helps support our work, but does not affect what we cover or how, and it does not affect the price you pay. Neither ZDNET nor the author are compensated for these independent reviews. Indeed, we follow strict guidelines that ensure our editorial content is never influenced by advertisers. While visiting any of the sites you find on those Wiki sites, do not maximize your browser, as it can help identify you by your monitor resolution. In this guide, we’ll show you what you need to know about how to access the dark web and how to keep yourself safe while you use it.
The website allows visitors to view all the goods and services on display before they buy something. The quantity, price, and characteristics of the product are all provided. However, the platform lacks an advanced search option and a wallet-free payment option. The ASAP is a moderate design marketplace on the dark web that offers helpful tools like mandatory PGP encryption and two-factor authentication for a safe browsing experience.

But if you connect to the VPN before connecting to Tor and an IP leak occurs, only the VPN’s IP address will be exposed. This is a free service that lets you upload images to share them with other people. It’s great for people who live in or travel through restrictive countries to securely access and use image hosting and sharing services, which might be unavailable.
- Additionally, many Internet Service Providers (ISPs) flag Tor usage as suspicious and may block access to the network altogether.
- As long as you are not looking for anything illegal in the real world, it’s perfectly legitimate to use the dark web to find whatever you need.
- For example, your Geekflare.com—your trusted business resource for growth exists on the surface web.
- The articles are in-depth and informative, and the site is completely free to access — no random paywalls pop up in the middle of articles.
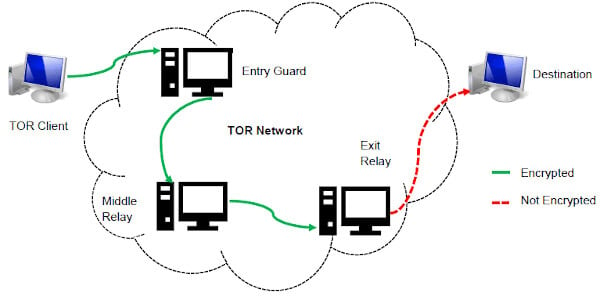
- Next step – your request will be transferred to Tor entry nod which in turn transfers to one or more Tor relays.
Should Governments Regulate AI-Powered Cybersecurity Tools? Balancing
Always run the latest version of the Tor Browser to protect against security vulnerabilities. Outdated versions may contain weaknesses that attackers can exploit to compromise your anonymity. I recommend enabling automatic updates and checking for new versions before each session. Get the latest in privacy news, tips, tricks, and security guides to level-up your digital security. If you only want to mask your IP address and don’t need to access the dark web, then going online with a VPN is much easier and faster than using Tor. Activists, whistle blowers, and journalists also use the dark web to communicate securely with sources and news organizations.

The Hidden Wiki — Collection Of Popular Dark Web Links
To do that, you’ll need a dark web search engine like Torch or Ahmia. These forums are frequently accessed via the top 10 dark web search engines, serving as essential resources for information and networking. Crypto services use various measures to keep cryptocurrency wallets secure and make sure your Bitcoin is safe.
Discover Unique Resources On The Best Tor Websites
Let’s dive into the heart of the dark web and explore its hidden corners. When you visit an onion site, your connection is routed through multiple nodes, each adding a layer of encryption. The dark web operates on a principle of anonymity, using tools like the Tor browser to shield users’ identities. This anonymity can be a double-edged sword—offering privacy for legitimate users while also serving as a refuge for cybercriminals.

Take Extra Security Precautions
Yes, but you need to be cautious because there are many malicious sites on the dark web. The best way to do that is to get the link from legitimate sources, like The Hidden Wiki. What’s more, you should always use a VPN (like ExpressVPN) with Tor to protect yourself from IP leaks. I also recommend using an antivirus (like Norton 360) to protect your device from malware infections. I also like that the security guides are user-friendly — the format is easy to scan, complicated terms are explained very well, and there are videos and screenshots. It’s great how the site has a Security Scenarios section too, where it offers personalized security tips for specific audiences (activists, academic researchers, journalists, and more).
What Is Phobos Search Engine?
They are part of the dark web and often provide anonymity for both users and service providers. DuckDuckGo is one of the leading private internet search engines on the open web. It’s so secure and privacy-oriented that the Tor browser uses it as the default search engine. Empire Market is a dark web shop that resembles the AlphaBay marketplace.
Web crawlers run the regular internet, scouring the web to discover newly published websites or pages in a process called crawling. Samson has over 3 years of experience writing about VPNs for Cloudwards. Apart from his professional endeavors, Samson is passionate about soccer and enjoys reading, table tennis and watching sports in his spare time. He has also contributed to platforms like Financesonline.com and Timeero.com. However, though the dark web is synonymous with nefarious activity, it does have some benefits.
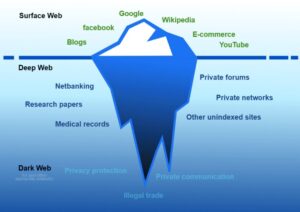
It’s a popular choice for users worried about online surveillance and data collection. Dark web websites are pages that exist on a part of the internet that isn’t indexed by traditional search engines like Google. Also known as deep web sites, these pages typically have URLs ending in .onion and are only accessible through special software like the Tor Browser. Anonymity of the dark web is one of the main draws for using onion sites, and most dark web links use a “.onion” domain.
Use A VPN To Access The Dark Web
The BBC, among others, is blocked in countries like North Korea or China because of the government’s strict censorship policies. This is why the BBC news website has established a unique .onion site, enabling anonymous access, via Tor, to its content without being subject to censorship, regardless of the location. The BBC Tor Mirror is a dark web site that provides uncensored news access. Sci-Hub has nothing to do with science-fiction literature, but with science itself.
Are Dark Websites Illegal To Use And Visit?
She holds a Bachelor’s degree in Liberal Arts and a triple Master’s degree in Literary and Cultural Studies. Outside of work, she is a travel enthusiast, music lover and avid learner interested in global cultures, spirituality, psychology and neuroscience. If you want to access the Tor network on your iPhone or iPad, you can use the Onion Browser app. The mobile app uses DuckDuckGo as its default search engine and is supported by the Orbit framework to provide secure access to the Tor network.