This article lists some of the best dark web websites you can visit securely. Some of these sites are very helpful (but unseen as Google doesn’t show them), while others are just for fun. A VPN will mask your location and stop the online breadcrumbs that can lead back to you. Connections made while a VPN is active will also be encrypted, helping you stay protected from eavesdropping and man-in-the-middle attacks.
How Do Individuals Get On The Dark Web?
Another challenge is CAPTCHAs; because Tor behaves differently than other browsers, it’s more likely to trigger the bot-hunting system, so be prepared to face more of them than usual. The dark web is infamous as a dangerous place, where drugs are bought and hitmen hired, but it can be a safe way to browse the internet if your privacy is serious concern. Your traffic is relayed and encrypted three times as it passes over the Tor network. The network is comprised of thousands of volunteer-run servers known as Tor relays. While Bitcoin and other cryptocurrencies provide some level of anonymity, blockchain analysis tools can trace illicit transactions. Organizations like WikiLeaks and investigative journalists use dark web platforms to exchange sensitive information safely.
To stay safe on the dark web, use a reliable VPN, avoid clicking on unfamiliar links, confirm URLs, and never provide personal information. Norton VPN fortifies your internet connection with ultra-secure AES-256 encryption, masks your IP, and never logs your activity. And, with an automatic kill switch that guards against unexpected exposure if the connection drops, you can enjoy powerful privacy protection as you navigate even the darker corners of the web. ProPublica is an investigative news site owned by an independent nonprofit that exposes abuses of power and corruption.

All Our Services
- It is dangerous because it contains many fake links, unreliable markets, and risks of police or hacker intervention.
- Add to that the fact that Bitcoin is the preferred currency on the dark web.
- Unlike traditional search engines like Google or DuckDuckGo, Torch indexes hidden websites that operate beyond the reach of the surface web.
- Many dark internet users favor Tor which uses a network architecture originally developed by the U.S.
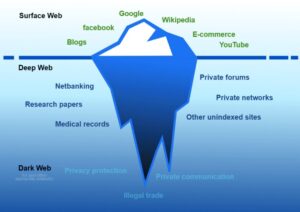
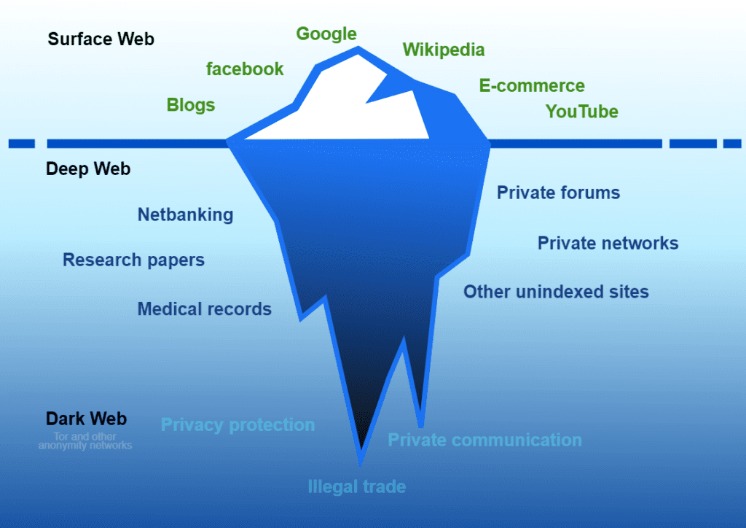
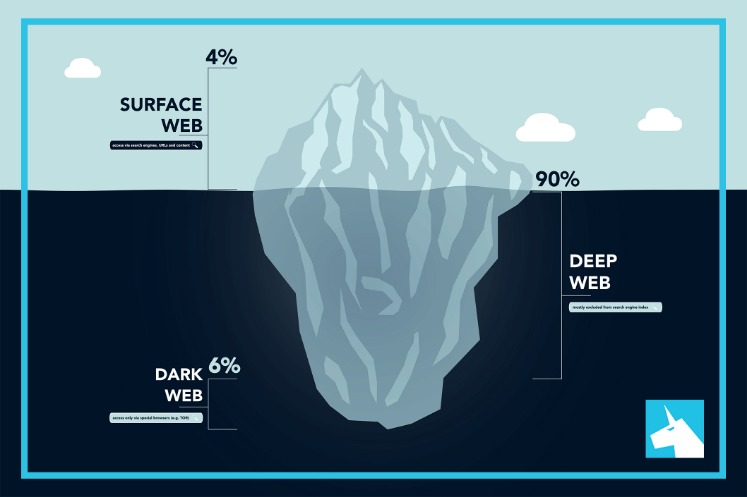
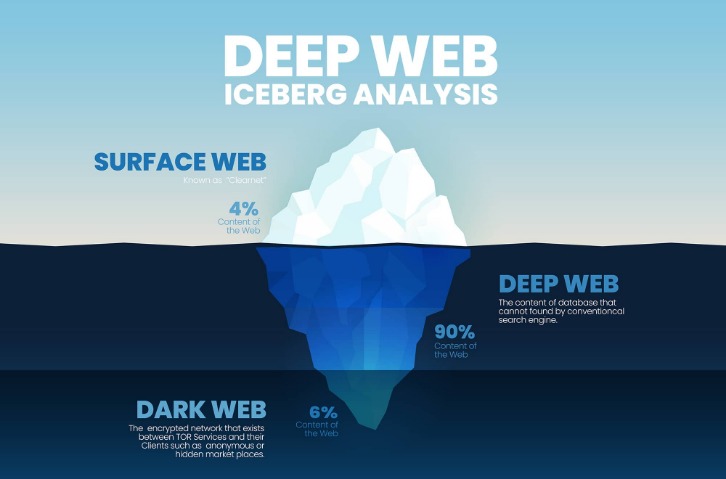
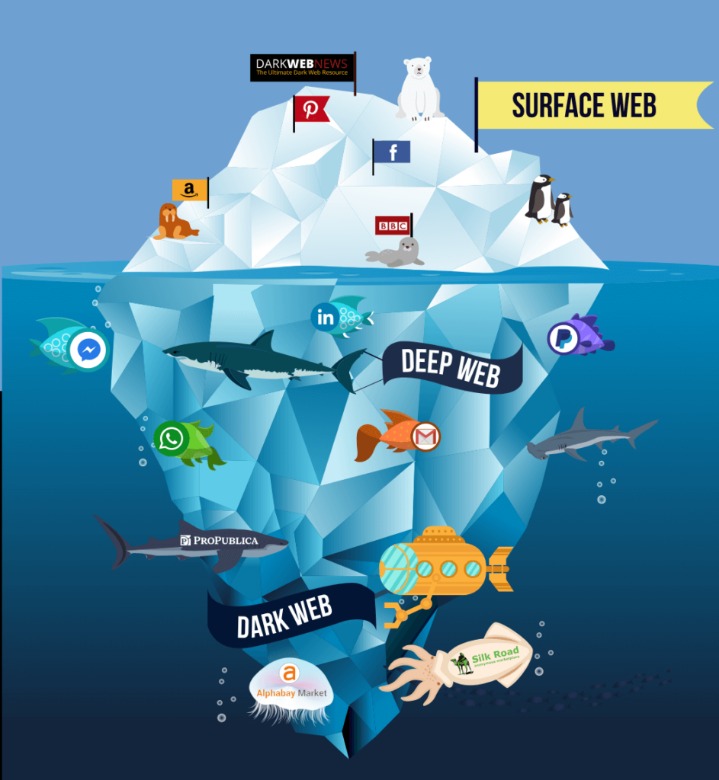
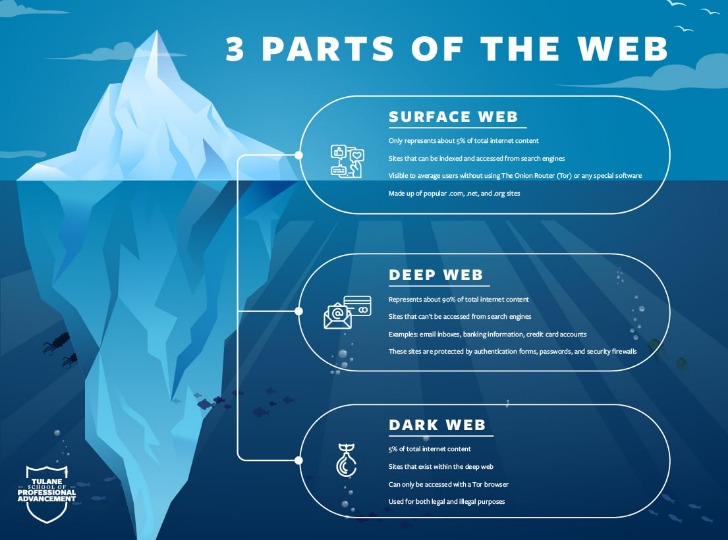
- The dark web is a hidden part of the internet that can be accessed through limited resources.
- The multiple relays help keep some distance and anonymity between the person visiting the website, the website itself, and any entity trying to eavesdrop on the communication between the two.
It offers outstanding privacy features and there is currently a discounted rate available through this link. Also, there’s a vast amount of unsavory content on the dark web, as well as a significantly high number of hackers and scammers looming on the platform. This allows you to use the computer without the risk of corrupting your computer’s normal operating system with viruses or malware. Tails also protects you from possible malware, viruses, or keystroke loggers that may have already infected the computer, as it doesn’t run the operating system already installed on the device. You can either sell or buy goods on the dark web, but both present difficulties. In opennet mode, the network will automatically assign you to other users on Freenet’s network.
Continue Reading About What Is The Dark Web (darknet)?
Illegal software, fake documents, and hacking services are all part of this underground market. The dark web stays hidden through special tools like the Tor browser, which uses onion routing to protect user identities. In onion routing, your internet traffic is encrypted and bounced through multiple volunteer-run servers around the world. This makes it extremely difficult to trace where a request comes from or where it’s going. The dark web is a hidden part of the internet that stays out of reach for normal browsers and search engines.
But contrary to popular belief, not everything found on the dark web is criminal in nature. In fact, some corners of the dark web exist to protect free expression and privacy where such rights are restricted or surveilled. Further explore why enterprise dark web monitoring is worth the investment. Regardless of being a business, parent, or any other user of the web, you’ll want to take precautions to keep your information and private life off the dark web. Just because the dark web feels anonymous doesn’t mean it’s invisible—especially to U.S. authorities. Accessing the Dark Web requires cautious navigation, and adhering to certain tips can help ensure a safer and more secure experience.
You can also use the Tails operating system to further protect yourself. If you’re just browsing the dark web out of curiosity, Tor, or a Tor and VPN configuration is safe enough. If you’re trying to hide from an oppressive government or want to be a whistle-blower for something illegal, take as many steps as you can to be safe. That’s why privacy-focused users often combine Tor with end-to-end encryption tools like PGP or services like Mailfence, which support secure, encrypted communication even outside of hidden networks. The dark web significantly influences the cybersecurity landscape, acting as a hub for cybercriminals to exploit vulnerabilities and trade illicit goods. One of its most concerning impacts is the sale of stolen data, including personal information, financial credentials, and intellectual property.
Tor Vs VPN: What’s The Difference?
Hackers stole the data and threatened to upload it to the web if the site did not close down, and they eventually acted on that threat. The spouses of Ashley Madison users received blackmail letters demanding they pay $2500 in Bitcoin or have the infidelity exposed. Infamous examples of Dark Web sites include the Silk Road and its offspring, such as Dream Market.
Types Of Threats Associated With The Dark Web
That’s why, if you’re planning on using the dark web for legal, privacy-focused reasons, it’s important to stay protected. Norton includes a bundled VPN and advanced malware protection to help keep you safe while browsing the dark web. It’s possible to buy and sell illegal drugs, malware, and prohibited content in darknet marketplaces. Some dark web commerce sites have dangerous chemicals and weapons for sale. Other dark web search engines include Not Evil, Torch, Haystack, and Ahmia.
VPNs That Work With The Darknet
However, there are possibilities that someone can still link personal details to a transaction due to issues like connected nodes, address reuse, and blockchain analytics. It also has inbuilt productivity tools such as a processor and an email client, which means once you’ve got TAILS installed, you can do much more than just browse the web safely. The best way to clear the traces is by installing the Amnesic Incognito Live System (TAILS) – a unique Debian-based version of Linux that removes the user activity on the computer. Due to its hidden nature, the dark web is also famous for the names underground internet and black web. However, don’t get scared of this frightening concept than the actual meaning of the dark web.
Unlike the surface web, which is open and indexed by search engines like Google, the dark web operates on encrypted networks that provide a high level of anonymity. A VPN adds an essential layer of security when accessing the dark web. By encrypting your internet connection and masking your IP address, a VPN prevents your ISP or other third parties from tracking your online activity. This is particularly useful for dark web browsing, as it provides an added layer of anonymity and protection. When combined with Tor, for example, a VPN can help prevent IP leaks and make it more difficult for network operators to trace your activities. The Dark Web is indeed the place where malicious actors sell, trade, and otherwise share illegal collections of data and illicit goods.
What Is The History Of The Dark Web?

Any traffic sent through Tor Browser is automatically anonymized and encrypted via many different hosts. The browser also has built-in protection for many kinds of tracking and de-anonymization features. This is just like any other browser such as Google Chrome or Microsoft Edge, except it can also access special website addresses which ends in .onion instead of .com and such.
Once a user installs a dark web browser on a device, it functions like a regular browser. That said, it can be difficult for users to find the material they are looking for on the dark web. Addresses tend to be a mix of random numbers and letters, making them challenging to remember or access manually. Addresses also change frequently due to the transient nature of many dark web actors. Finally, because the dark web routes all traffic through a series of proxy servers, which are operated by thousands of volunteers around the world, the search process is typically very slow. The dark web offers both benefits and risks for users going into it, but the intent of the user will also impact this.