Individual apps are configured separately to function with I2P, whereas a web browser’s proxy setting must be configured to use the correct port. Furthermore, the VPN offers a dedicated dark web feature called Dark Web Monitoring that alerts you if your privacy has been breached or some of your login credentials are available on it. The VPN has a vast and well-established network, with 6,000+ servers spread across 111+ countries. When exploring the deep web, this VPN will offer fast and stable connection speeds on most servers. The readers like you support Beencrypted to help keep up the good work.
Step 2: Install OnionShare On Whonix Workstation
However, its opaque filtering process and unstable .onion address require caution, making it best for users seeking a balance of safety, simplicity, and breadth. Think of it as the dark web’s yellow pages, curated by anonymous volunteers who add, update, or remove links. The Hidden Wiki supports V3 .onion addresses and blocks some malicious sites, but its reliance on community moderation leads to inconsistent quality.
Can I Access The Dark Web With A Free VPN?
When browsing the dark web on mobile, finding what you’re looking for can be tricky. Dark web search engines are the gatekeepers to the Tor network’s hidden corners, empowering users to explore what’s intentionally unindexed. Businesses can scan for leaked data or cyber threats using premium engines like Haystak for monitoring forums and marketplaces. Integrate with tools like dark web monitoring services for alerts on credentials or IP theft. Engines like Ahmia or NotEvil require Tor for encrypted, untraceable searches, whereas deep web crawlers (e.g., for academic databases) use standard browsers and APIs without anonymity emphasis.
Step 2: Download And Verify The Tails OS Image
Regularly scan your system for any malicious software or vulnerabilities. Use common sense and trust your instincts when navigating the Dark Web. If something seems suspicious or too risky, it’s better to err on the side of caution and avoid it altogether. Onion websites operate differently from regular websites on the surface web.

Mobile Optimization And Accessibility
NotEvil’s inclusion enhances the guide’s value, offering a privacy-centric, ad-free engine that bridges Ahmia’s safety and Torch’s scope. These newcomers focus on user trust and cross-network support (e.g., I2P), but verify their .onion stability via communities. They complement established ones like NotEvil, offering fresh features for niche research. Trends like trust metrics and mobile optimization will enhance usability, but regulatory pressures may increase ethical moderation. In 2025, engines like Ahmia and NotEvil are invaluable for journalists, enabling anonymous discovery of whistleblower platforms (e.g., SecureDrop) or leak forums without surface web surveillance.
- The best way to find out is to check the “Have I Been Pwned” (HIBP) website.
- In 2002 the dark web began to grow significantly when researchers backed by the U.S.
- You need the right setup, a cautious mindset, and zero tolerance for shortcuts.
- It protects your real IP address even if Tor leaks, is easier to set up, and works with most major VPN services.
Major Risks When Browsing The Dark Web
This expanded section details how to use dark web search engines like Ahmia, NotEvil, or Torch securely, drawing on my 15 years of tech exploration to provide a comprehensive, actionable guide. You might think the dark web is a place of pure mystery, but really, it’s a realm of both intrigue and utility. Whether you’re curious or cautious, accessing it on your phone is not as daunting as it seems. The right tools, like Forest VPN, can help you explore safely and securely. Let’s unpack the steps and safety measures you’ll need for this expedition.
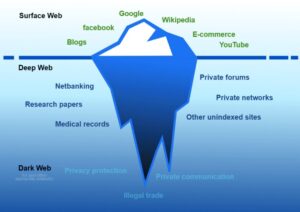
That means that only 0.024% of all the known pages are findable in Google’s search engine. The users only have access to a fraction of the available data and web pages. The RAT allows its creator to hijack your webcam and spy on you through your device’s camera lens. To mitigate this threat, be vigilant of any links you click on and do not download any files. Moreover, it is best to cover your webcam with tape or paper if you are not using it. Sometimes, a dark web user on any of its open forums can also attempt a phishing attack to steal your personal information and further use it for financial gains or identity theft.

Good Password Ideas And Tips For Secure Accounts
This makes sure your messages are encrypted and only readable by the recipient. Common payment methods are tracable, so keep to cryptocurrency; bitcoin or monero. But know that Bitcoin is not completely anonymous — use mixing services to hide your blockchain transactions. It’s also about practicing good operational security (OpSec) to help protect yourself and your money. One of the hardest parts of the dark web, in fact, is finding reliable marketplaces. They can monitor exit nodes but cannot easily trace traffic back to individual users unless mistakes are made.
My Take: Why Dark Web Search Engines Are Essential
In 2025, NotEvil helped me find a privacy tool safely, but a risky marketplace link slipped through, avoided only by verification. These experiences taught me to use Tails OS, verify links, and stick to filtered engines for sensitive work. However, privacy risks (e.g., AI tracking, regulatory overreach) demand vigilance. Staying updated via r/onions, tor.taxi, or security blogs will be crucial to leverage these advancements safely. New engines like VormWeb categorize results by safety (secure, moderate, risky), a trend likely to dominate by 2026.
Bitcoin’s popularity stems from its widespread adoption, while Monero is preferred for its robust privacy capabilities. These digital currencies are shielded by advanced encryption technologies, facilitating anonymous, seamless transactions without reliance on a central authority. Law enforcement agencies are constantly striving to trace and combat illegal activities on the dark web. VPN stands for virtual private network, and it acts as a security bubble for communications from your device. A VPN automatically encrypts your data as soon as it leaves your device through the VPN server. This means your private information, location, and any communications you send are hidden and protected.
However, your access is limited to the information that the website’s administrator permits you to see. Navigating the Dark Web may be dangerous, as it is frequented by cybercriminals, hackers, and law enforcement organizations. To safeguard oneself while exploring this secret environment, employ safe browsing behaviors, such as maintaining anonymity. Avoid giving personal information or participating in activities that may jeopardize your anonymity. As you venture into the Dark Web, it is vital to remember that the Dark Web carries risks.

In other words, purchasing bitcoin via a service that requires you to complete know your customer (KYC) identification does not preclude you from spending those coins on the darknet or elsewhere. Darknet markets (DNMs) supply all manner of goods, some legal, others less so, but all purchasable with cryptocurrency and delivered to your door. Indeed, many people’s first exposure to bitcoin is when they have the need to purchase something off the darknet.
Sending Group Texts On Pixel 6: The Definitive Guide
- The VPN provides data encryption and routes your data through remote servers to help mask your IP address and location.
- Severe vigilance and preparedness are needed to follow any footsteps here, from using a good VPN and secure browser to staying strictly anonymous.
- Syed Balal Rumy is a seasoned cybersecurity writer and dark web researcher with over 15 years of experience exploring the internet’s hidden corners.
- That said, illegal actions remain illegal, whether on the dark web or not.
- Active since around 2019, Torlinks is a directory-style tool that complements dark web search engines by offering a curated index of V3 .onion links.
This adds an extra layer of security by requiring a second form of authentication, such as a unique code sent to your mobile device, in addition to your password. Stay informed about the latest security practices and developments related to the Dark Web. Regularly educate yourself about new threats, scams, or vulnerabilities that may arise. This will help you adapt your browsing habits and maintain a safer online experience.
A method of mitigating malware attacks is to ensure robust endpoint security. Make sure to protect your device with reliable anti-malware to mitigate such attacks. A virtual machine is a file that behaves like your computer while virtually borrowing a dedicated amount of CPU storage and memory from it. It runs in a different environment and is partitioned from the rest of the host system.
Before you go much further, it’s important that you close out of other applications and software that offer malicious users on the dark web an entry point into your device or network. When closing down other applications it’s important to actually right-click and quit rather than just hitting the x in the corner of the window. That being said, the anonymity offered by the dark web is the perfect breeding ground for criminals from all walks of life and users are advised to browse with extreme caution.