
Using bitcoin and accessing the darknet for the first time can be bewildering. With a little practice, though, it soon feels second nature and you’ll become comfortable at placing orders with relative ease. From there, it will be a rapid progression to discovering the many other things you can do with cryptocurrency. If you’re a beginner, and would prefer an easier way to buy bitcoin, you could install the Bitcoin.com Wallet, available for Android or iOS. Follow the setup instructions, including making a copy of the 12-word wallet recovery phrase that’s shown on-screen.
We showed that some of the links of this user-to-user (U2U) network are ephemeral while other persist in time. We highlighted that a significant fraction of stable U2U pairs formed as their members were trading with the same DWM, suggesting that DWMs may play a role in promoting the formation of stable U2U pairs. We showed that the relationships between users forming stable pairs persist even after the DWM shuts down and are not significantly affected by COVID-19, suggesting overall resilience of stable pairs to external shocks. Similar results hold for the full network, confirming that the formation of U2U pairs is a pervasive phenomenon around DWMs. The total trading volume users sent to DWMs was $3.8 billion, volume received from DWMs was $3.7 billion, while the volume exchanged through U2U pairs reached $30 billion.
- Similarly, there is no unique choice for the classification parameters or ground truth for fitting them.
- Over time, ambitious individuals created infrastructure for these transactions, where for a fee, sellers have access to a digital ‘storefront’ to sell their products in a centralized marketplace.
- In each network, links are directed and the arrows point at the receiver of Bitcoin.
- Historically, the largest users of Bitcoin Fog were darknet markets such as Agora, Silk Road, Silk Road 2.0, Evolution, and AlphaBay.
- Typically, the publication Bitcoin Magazine doesn’t cover Bitcoin Cash topics, but the news outlet’s Aaron van Wirdum wrote an objective article on the new privacy protocol for BCH.
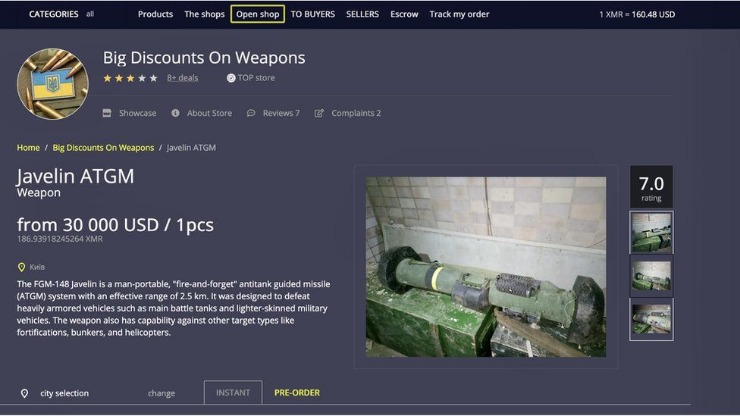
Torrez Market
Unfortunately, Lightning has privacy flaws when it comes to receiving money. For instance, the receiver needs to provide his “channel point” when creating an invoice. A channel point is the UTXO on the blockchain that is used to back the channel with on-chain bitcoin; that means that the sender can view the receiver’s on-chain transaction history.
Why Security Leaders Prefer To Buy CTI Solution For SaaS Platforms In 2025
Waugh disclosed he queried a number of transaction inputs and outputs and realized that it’s “not possible to establish a concrete link” between them. Essentially, Cashfusion in Waugh’s opinion is far more practical than other Coinjoin protocols. Hudson Intelligence assists law firms, businesses, public agencies and investors with cryptocurrency investigations and due diligence.
Like other marketplaces, it also requires registration for new users and accepts payments in Monero. Sterlingov, 35, was found guilty of money laundering conspiracy, sting money laundering, operating an unlicensed money transmitting business, and violations of the D.C. District Court Judge Randolph D. Moss scheduled sentencing for July 15, 2024, and will also consider a further forfeiture money judgment.
Share This:
Its ring signatures and stealth addresses obscure transaction details, providing a level of security that Bitcoin lacks. To study the performance of sellers, we analyse the quarterly median income, i.e., the quarterly median of the money received by each seller, for each category and multisellers, as shown in Fig. We find that multisellers have the largest median income throughout the period of observation—except in the last quarter of 2017 and 2018, when they have the second largest median income. They are followed by market-U2U sellers, then market-only sellers, and lastly U2U-only sellers. Therefore, although larger in number, U2U-only sellers typically make the smallest income. This suggests that sellers with more diverse sources of income, such as multisellers and market-U2U sellers, are able to produce a higher income.
Implications For Security Leaders
Regulators are filling Anti-Money Laundering (AML) and Know Your Customer (KYC) loopholes to enhance compliance and traceability. International collaboration is needed to fill the gaps in jurisdiction and avoid exploitation. Smooth digital asset integration demands a well-considered strategy seasoned with innovation, regulation, and proactive risk management to make a secure financial future a reality. Law enforcement agencies are also increasingly dedicating resources to counter darknet markets specifically. This includes the establishment of specialized teams, such as the Joint Criminal Opioid Darknet Enforcement team, or J-Code, which was created by the FBI in 2018 and brings together specialists from various agencies.
Our research shows that, like most legal commodities, stolen data products flow through a supply chain consisting of producers, wholesalers, and consumers. But this supply chain involves the interconnection of multiple criminal organizations operating in illicit underground marketplaces. Unlike Monero, which requires specialized knowledge and access to smaller, less reputable exchanges, Bitcoin remains widely available and can be easily converted to fiat currency. Although Bitcoin transactions are not inherently private, darknet users have found ways to enhance anonymity through coin mixing services and privacy-focused wallets. For years, Monero had been the preferred cryptocurrency for illicit transactions on the darknet. Unlike Bitcoin, which operates on a transparent blockchain where all transactions can be traced, Monero offers enhanced privacy features, making it an attractive option for those seeking anonymity.
This process controls how many of the cryptocurrencies from the global market are represented on our site. Circa the late 2000s, a technological prodigy pseudonymously known as Satoshi Nakamoto birthed a new form of digital currency, Bitcoin. At this time, the surface-level internet was already an established entity, but the Darknet was barely sprouting its clandestine roots.

Q: Why Do Darknet Markets Prefer Bitcoin For Transactions?
For instance, you can choose the preferred security levels for enhanced protection. The security level is set to ‘Standard’ by default, but you can change it to the ‘safest’ and enjoy more security while accessing the dark web. Having JavaScript enabled on the dark web can cause havoc because it can reveal your IP address to your website. Also, previously, the Tor browser was vulnerable to JavaScript attacks as it provided hackers a pathway to track your activities by using the session details. Therefore, for security reasons, disable JavaScript on the Tor browser and enjoy an anonymous browsing experience on the dark net.
Cypher marketplace has been on the list of the best dark web shops for a while and deals with the business of a variety of products and services. The shop accepts payment through Bitcoin and Monero, while some vendors accept the coins. As these marketplaces keep changing, it is critical to stay on top of the main platforms on the dark web worth monitoring.
Access This Article
The White House market offers impressive features like a mandatory PGP requirement that enables 2FA for the user’s profile and adds a protective layer. Below are the best marketplaces on the dark net that we hand-picked after going through multiple shops and doing extensive research. When transacting, make sure it’s peer-to-peer and not through an exchange or other intermediary. Never use a custodial wallet — you can not ensure your privacy if you count on a third party to take care of it for you. Also, when acquiring bitcoin make sure to use a non-KYC (know-your-customer) exchange.
Trump Admin Silent As Tornado Cash Verdict Threatens Bitcoin Privacy
- The dotted line corresponds to the result of a fitted power law function.
- Darknet markets have surpassed their 2019 revenue this year with a month to spare, according to a report published by Chainalysis yesterday.
- Therefore, we analyse the temporal network where nodes are the active markets and an edge between the nodes represents the number of multibuyers between them, what we henceforth call the multibuyer network.
- Users interacting with other users form U2U pairs and we include them in our dataset.
- Valued at approximately $15 million, Abacus Market is one of the most lucrative platforms in the dark web ecosystem.
Emerging threats include AI-driven scams and crypto ATM fraud, which target vulnerable users. Strengthening KYC/AML regulations, enhancing blockchain analytics, and increasing consumer awareness are crucial in combating these cyber threats and protecting investors from financial losses. The cryptocurrency space remains vulnerable to scams that exploit investor trust and security weaknesses.

Step 2: Accessing The Darknet
The resulting data set includes for each transaction the source and destination entities, the time, and the value of the transaction. This suggests that the multiseller activity is sensitive to external shocks but also that it yields higher profits. The structural change in the multiseller network and the resilience of the multibuyer network. Temporal network of multisellers (top) and multibuyers (bottom) between markets for each year. Edges are multihomers, i.e., traders that are simultaneously active in both markets (sellers in the multiseller network, and buyers in the multibuyer network). The width of the edges is proportional to the number of multihomers acting between the markets.
In the U2U network, an edge connects nodes that are not necessarily users of the same market. Previous studies have shown that, although the number of users and transactions is larger in markets, the trading volume in the U2U network is larger than that of markets13. (a) The number of sellers for each category and multisellers per quarter.



