He follows the latest cybersecurity compliance updates and brings readers practical insights they can trust and keeps them ahead of the curve. On May 8, 2024, Ascension Health, a major U.S. healthcare system, suffered a ransomware attack by the Black Basta group. As a result, clinical operations across 142 hospitals were disrupted, causing an electronic health record outage that lasted nearly four weeks.
Decoding Credit Card Fraud On The Dark Web

In the ever-evolving landscape of cyber threats, businesses face not only financial losses but also significant reputational damage when targeted by fraud actors on the dark web. Monitoring the deep and dark web becomes imperative for proactive defense against such threats. Lunar, our dark web monitoring tool is designed to empower individuals and businesses in this battle against cybercrime. With features like real-time alerts, data breach monitoring, and comprehensive dark web post monitoring, Lunar helps organizations stay ahead of deep and dark web threats in an increasingly hostile digital environment.
AllWorld.Cards appears to be a relatively new player to the market for selling stolen credit-card data on the Dark Web, according to Cyble. “Our analysis suggests that this market has been around since May 2021 and is available on a Tor channel as well,” according to the post. When a hacker writes up new malware, steals a database, or phishes someone for their credit card number, the next step is often toward dark net marketplaces. These black markets allow buyers and sellers to make anonymous transactions using a combination of encrypted messages, aliases, and cryptocurrency.
- These measures include implementing robust security practices, such as encryption and multi-factor authentication, to protect credit card data and reduce the likelihood of it ending up on the dark web.
- It tracks changes to your credit report and helps you spot potential identity theft early, so you’re not the last to know when something goes wrong.
- Between June 19 and 21, 2024, Acadian Ambulance Service experienced a ransomware attack by the Daixin Team, compromising the protected health information of approximately 2.9 million individuals.
- Financial institutions shoulder increased operational costs tied to investigating fraudulent activities and failed authentication attempts.
- Anyone who uses credit cards for daily purchases should monitor for exposure to protect against fraudulent transactions and unauthorized access.
- The breach, discovered on August 6, exposed business contact information such as names, email addresses, and phone numbers.
Vance, Leavitt, Other Politicians’ Spotify Playlists Leaked
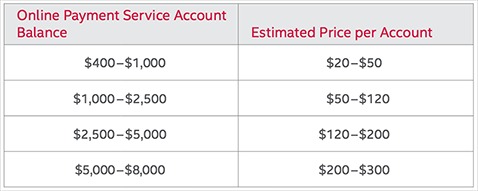
The average price for your personal information can range from as little as $1 to more than $4,000. The dark web can be accessed using the Tor browser, which is available for free online. However, it’s important to note that accessing the dark web can be dangerous and is not recommended unless you have a specific reason to do so.

Customers
This process involves customizable software tools and techniques designed to bypass security measures and validate the stolen card data. This type of fraud centers on the unauthorized use of a person’s credit card or debit card to make purchases or withdrawals. Once criminals have the card details, they attempt transactions—sometimes small, sometimes large—in order to test whether the card is still active.
Dark Web Monitoring Tools
While SSN, name, and DOB are all fairly standard in fullz, other information can be included or excluded and thereby change the price. Fullz that come with a driver’s license number, bank account statement, or utility bill will be worth more than those without, for example. These bundles of personal info are called “fullz“, short for “full credentials.” So instead of looking at the prices of SSNs on their own, Comparitech researchers analyzed the prices of fullz. Comparitech researchers sifted through several illicit marketplaces on the dark web to find out how much our private information is worth. Where possible, we’ll also examine how prices have changed over time.
Why Monitor Deep And Dark Web Credit Card Sites?
- Thousands of web applications worldwide could be at risk if HTTP/2 is enabled.
- From technological solutions like payment card BIN monitoring to simple practices like monitoring your financial statements, the key to protection lies in proactive and informed action.
- The breach resulted from a phishing campaign targeting IDHS employee accounts, leading to unauthorized access to personal information, including Social Security numbers, names, addresses, and public assistance account details.
- Threat actors discuss and share knowledge on new hacking techniques and tools.
- But if you share information by clicking on the link or responding to the email/text, the data goes directly to a hacker.
- The attackers secretly altered a digital wallet address, redirecting 401,000 Ethereum coins to their own wallet.
The UK Ministry of Defence set up a covert Afghanistan Response Route (ARR) following the breach. The program has since resettled 4,500 people, with another 2,400 expected, at a cost of £850 million. A successful attack could severely impact confidentiality, integrity, and availability of Teams data. The issue was one of 107 vulnerabilities patched in August, which also included a fix for a Windows Kerberos zero-day. Forum administrators also impose “sanctions” on individuals who break their rules, Mador adds.
Over Half Of Security Experts Overwhelmed Managing Cybersecurity Tools From Multiple Vendors
The stolen data reportedly includes a mix of credit and debit cards from major providers like Visa, MasterCard, American Express, and JCB. Wizardshop.cc was established in 2022, and offers a wide range of leaked CVVs, database dumps and even RDPs. In the past 6 months, the site has increased the volume of cards sold, placing itself as one of the top sites selling credit cards today. The site has a unique news section, where the admin updates the buyers about new leaks and dumps, the source of the dumps, structural site updates and more.

One of the main challenges has been inconsistent cooperation across crypto platforms. The exchange eXch allowed over $90 million to be moved through its systems before taking action. While ByBit’s CEO Ben Zhou emphasized that no customer funds were affected and the firm has replenished the stolen amount through investor loans, the company launched a Lazarus Bounty program.
Transactions can be quickly flagged or blocked, making fraud attempts risky and unreliable. As a result, carding communities are developing new strategies to leverage existing online platforms and withdraw money from stolen credit cards. The repercussions of dark web credit card marketplaces, including the rise and fall of Joker’s Stash, extend beyond monetary losses. Financial institutions shoulder increased operational costs tied to investigating fraudulent activities and failed authentication attempts.
Texas Tech Health Sciences Center Data Leak

Since it was established in 2020, Real and Rare has been considered to be a stable credit card site that suffered very few downtimes. The number of card packages offered on the site has consistently increased, and today it also has an active Telegram channel from which it operates and sells stolen credit card details and announces new dumps. After it relaunched in June 2022, BidenCash initiated a promotional campaign that included sharing a dump of 8 million lines of compromised data for sale, which included thousands of stolen credit cards. Implementing a 3-D Secure ACS solution, like Outseer 3-D Secure, fortifies the fraud prevention strategy. This EMV® 3-D Secure ACS delivers a secure, frictionless digital shopping experience, providing a multi-layered defence against unauthorized transactions. By adding an extra layer of authentication, financial institutions reduce the risk of fraudulent activities during transactions.
Spyware and malware attacks are another common tactic used by scammers to steal data, and they are typically a result of phishing schemes. Stolen card details often end up on the dark web marketplace for a quick profit, and this can happen before you even know about it. The consumer watchdog has been flooded with Optus-related scam complaints following the data breach. “Collecting and storing personal information that is not reasonably necessary to your business breaches privacy and creates risk,” she said.