Other free VPNs have more severe issues, such as 2-10 GB of monthly bandwidth and intrusive logging. Having the tools at your disposal but not knowing how to use them feels… incomplete?! To complete the final piece of the puzzle, let’s explain how to use these tools. If you want an in-depth guide, consider accessing the dark web safely with this tutorial from our experts. If not, Surfshark fully supports Tor and Onion over VPN connections that are native.
Get A Risk Free Trial
For users who are already part of the Proton ecosystem, such as those using ProtonMail, ProtonVPN offers seamless integration. This integration enhances the user experience by simplifying the protection of all digital communications under one umbrella. Tor Browser prevents someone watching your connection from knowing what websites you visit. All anyone monitoring your browsing habits can see is that you’re using Tor.
Notes From The Lab: CyberGhost Speed Test Results

Stay informed, avoid questionable undertakings, and use a secure VPN to explore safely from the comfort of your glowy screen. The choice is yours on how to proceed – now with your privacy fully protected. Always enable extra protections like DNS over HTTPS (DoH) using browsers like Firefox.
Free VPNs You Should Avoid
Some of them (the hardest ones to access) are situated in what is known as the dark web. Browsing the dark web safely requires more than just Tor — your ISP can still see you’re using it. With NymVPN, you get true anonymity, preventing ISPs and surveillance actors from tracking your activities, keeping your online identity hidden.
- If you need to protect or enhance your streaming, gaming, or torrenting activities, a Virtual Private Network (VPN) is a much better option as a secure connection to the net.
- It can only be used to access the content uploaded to the Freenet, which is a peer-to-peer distributed data store.
- Premium services are known for their superiority compared to free VPNs.
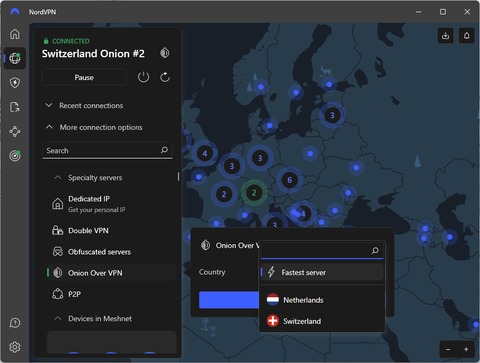
- Another aspect particularly interesting in the context of this page is NordVPN’s Onion over VPN feature.
- It is compatible with Windows, macOS, iOS, and Android, ensuring a consistent and user-friendly experience regardless of the device used.
Fun fact is that Tor Browser (Tor network is a different thing than the browser) is built from Firefox ESR (Extended Support Release), a modified version of Firefox. So, it’s worth using Firefox if you’re up for the tweaks needed. It uses sandboxing to keep each application isolated from the other, preventing a breach in one app from spreading across the whole OS.
The Best Free Dark Web VPN: Proton VPN
ProtonVPN secures the #1 ranking thanks to an unparalleled combination of high-level security, unmatched free plan, and dedicated servers optimized specifically for .onion routing. If you’re based in a country that blocks Tor traffic, use Astrill to bypass the online firewall and download the Tor browser. Our definition of a zero-logs VPN can collect personal information (an email address, username, password, and any payment data provided) and aggregate anonymous logs.
WANT TO TRY THE TOP VPN RISK FREE?

NordVPN is offering a fully-featured risk-free day trial if you sign up at this page . You can use the VPN rated #1 with no restrictions for a month – great if you want to binge your favorite show or are going on a short trip. The most common way to safely access the dark web is by connecting to a VPN and then opening the Tor browser. Its inherent anonymity allows everyone from dissidents to whistle-blowers the opportunity to share information free from persecution. In many cases, this information can itself be used to prevent illegal activities. This is because they lack the requisite security and protection protocols.
How To Access The Dark Web Using The Tor Browser?
- PureVPN is a great choice if you want to save money over the long term.
- As one of PrivacySavvy’s resident VPN experts, he guides readers on protecting their online information and anonymity.
- Many experts advise against using third-party mobile browsers that utilize the Tor Network.
- But the risks outweigh the benefits of using these servers because the Tor browser is the safest browser to use when accessing the dark web.
They allow you to employ additional VPN protection to Tor with a single click. Second, the VPN uses RAM-only servers and has Swiss-grade privacy thanks to a verified no-logging policy. We tested it with Tor numerous times, only to have a proper browsing experience with no slowdowns. Mind you, this applies to all platforms on which Tor is available, which I could utilize to the fullest thanks to 7 simultaneous connections.
Free VPNs also limit your speeds considerably, which will be frustrating on the dark web since it’s already slowed down with Tor. CyberGhost VPN uses secure RAM-only servers, doesn’t collect your data, and offers incredibly fast speeds. Try it out with our 45-day money-back guarantee to see for yourself. The split tunneling feature offers users the ability to manage their VPN connection more efficiently, allowing them to decide which apps use the VPN and which don’t. This can be particularly useful for accessing local websites or streaming content without a VPN, while still protecting the traffic that requires more security or anonymity. Unfortunately, the kill switch is only available on the premium plan, so it’s a bit riskier to use than hide.me, which includes an app-based kill switch for free.
It has a large network of secure servers, the ability to keep connections private, and apps that are rich in security features. TunnelBear is a reliable free VPN provider that allows users to visit the dark web safely. The VPN provider uses the highest encryption standard, such as AES-256-bit, to encrypt incoming and outgoing traffic. In addition, it uses SHA-256 for data authentication and multiple handshake encryption keys depending on the device you use to access the dark web. It encrypts your connection, hides your IP address, providing protection when accessing the dark web.
This provider’s apps are packed with tiny features you’ll find handy. For example, OpenVPN and WireGuard can be customized to fit your needs. You can enable Multi-hop to double your encryption or use MACE to squash and destroy all trackers, pop-ups, and ads. Private Internet Access focuses primarily on privacy, security, and server distribution. The first two are essential, especially when you have features like Multi-hop, a kill switch, split tunneling, and WireGuard. Having in mind the dark web’s “shadowy” reputation, opting for the most secure VPN is always a good thing.
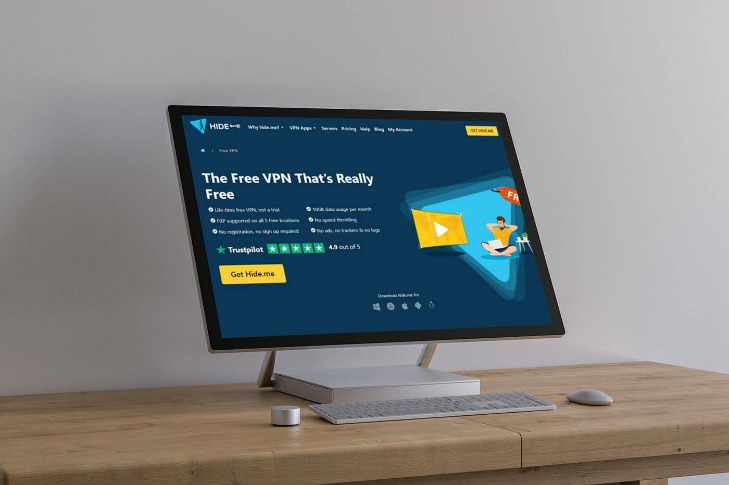
Secure And Private Free VPN Service
We tested them with Tor, and they passed the baseline for privacy, encryption, and stability. On that note, if you’re having trouble telling the two apart (including their strengths and weaknesses), check out our comparison of Tor and VPNs. Read our posting guidelinese to learn what content is prohibited.