
This allows you to go online anonymously and without ISP monitoring. The key is to encrypt your traffic BEFORE you use Tor so that your ISP (Internet Service Provider) doesn’t see you’re in the Tor network. You need a special browser (Tor) and all of these websites are intentionally obscured. So, to clarify again, this tutorial will cover how to access the dark web privately and safely – not the deep web.
- Indeed, most nations; including the United States, the United Kingdom, and India, allow access to the dark web as a lawful activity.
- The content management system into which I am typing this article is on the Deep Web.
- A VPN encrypts your internet connection and masks your IP address, making it difficult for anyone to trace your online activities back to you.
- This means you can go on the darknet privately while downloading torrents on the side.
- However, this feature is only available on iOS, Android, and Windows.
Should I Only Use A VPN To Access The Dark Web?
ZeroNet is a decentralized, peer-to-peer network that allows users to create and host websites without the need for a centralized server. It provides anonymity and censorship resistance and is available for Windows, Mac, and Linux. One of the earliest and most well-known dark web marketplaces was the Silk Road, launched in 2011 by Ross Ulbricht. The site allowed users to buy and sell drugs, weapons, and other illegal goods using cryptocurrencies such as Bitcoin.
Anatomy Of A Data Breach

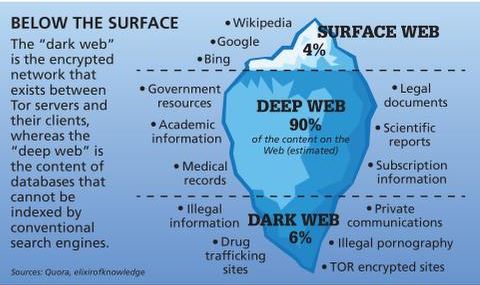
To access the Freenet-based dark web, you need to install the Freenet application. The dark web, a subset of the deep web, cannot be accessed with a regular browser. It hosts encrypted websites, often used for privacy, anonymity, or illicit activities. The surface web is the open part of the internet, which includes publicly accessible websites and resources. Search engines index all the web resources on the surface web, so you can search for them online. You just need standard browsers like Chrome, Edge, and Safari to open websites on the surface web.
Can WiFi Owners See Your Internet History?
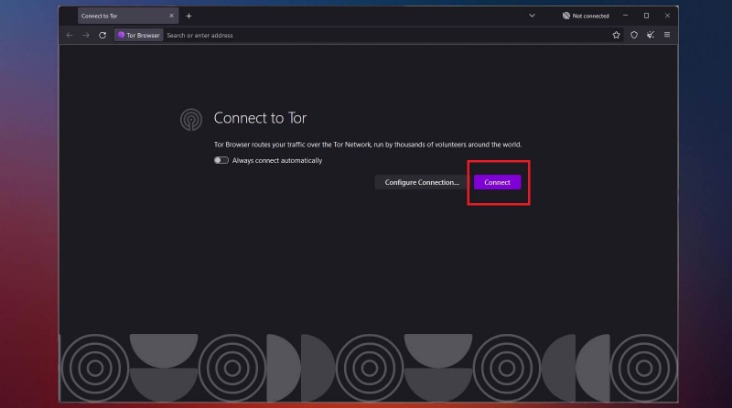
You need special tools to access the dark web, and the Tor Browser is the safest and most popular one. Make sure you download the Browser from the official website (torproject.org). Downloading and installing the Tor Browser should only take you 2–3 minutes.
Step 1: Use A Secure Device
Unfortunately, some oppressive regimes have figured out a way to block Tor traffic. Tor Over VPN is when you first connect your computer or mobile device to your VPN service and then use the Tor Browser to travel the internet. Each of these nodes removes or “peels” away a single layer, which uncovers the data’s next node destination. When the final layer of the “onion” is reached and decrypted, the message arrives at its destination. In this comprehensive guide, I will endeavor to answer those questions and many more. I’ll go into how the Tor system works, explain the Onion Network, what a relay is, and how to make the Tor Browser work best to protect your online privacy and anonymity.
Tor can be used together with a VPN to provide overlapping layers of privacy and anonymity. The quickest way to access the dark web is to download and install Tor Browser, which will route your traffic through the Tor network and let you access the dark web. On Tor, you can type in any URL you’d like to visit, including .onion links on the dark web. The difference between the dark web and the deep web is that the deep web refers to websites and web pages that aren’t indexed by search engines, like login pages and payment portals. The dark web, by contrast, is configured on darknets — online networks that can be accessed only with special software and techniques. The dark web refers to content on the internet that is intentionally hidden and requires special software like Tor Browser to access.
To understand how this is possible, we need to see how the web has many layers, and not all content is publicly available from a search engine query. Just because the dark web feels anonymous doesn’t mean it’s invisible—especially to U.S. authorities. Accessing the Dark Web requires cautious navigation, and adhering to certain tips can help ensure a safer and more secure experience. The beginning of the dark web is generally seen as coinciding with the release of Freenet in 2000. As the thesis project of Ian Clarke, a student at the University of Edinburgh in Scotland, the Freenet was built to help people anonymously communicate, exchange files, and interact online.
Cybercrime Services

Subgraph OS is a Linux-based operating system designed for security, privacy, and dark web access. Built with multiple layers of security and Tor integration, it provides a robust environment to prevent malware attacks and safeguard user data. The browser routes your traffic through a global network of volunteer-run servers (sometimes called nodes), encrypting your data and masking your IP address multiple times.
Antivirus will ensure that any viruses or malware downloaded from the dark web are removed. Accessing the Dark Web safely in 2025 demands vigilance, preparation, and strict adherence to security best practices. By carefully following the safety procedures outlined in this guide, you minimize your risk of encountering malware, fraud, or legal troubles. Always remember, your safety online depends significantly on personal responsibility, informed decisions, and proactive application of security tips. Embrace these strategies to confidently navigate the Dark Web, preserving your privacy and security in an ever-evolving digital landscape.
How To Access onion Sites Safely

With dangers like this in mind, it’s even more important to stay safe when surfing the Dark Web than any other part of the internet. Search engines such as Google search an index of websites, using links to form a hierarchy of results based on everything from temporal relevance to keywords. A common misconception about the internet is that, once you open google, you can access anything and everything available online. In fact, only about 5-10% of the information on the internet is available through common browsers like Google Chrome or Mozilla Firefox, known as the ‘surface web’. This guide will cover the top dark web browsers, how they work, and the security benefits they offer.
The “onion routing” technology underpinning the dark web was developed by researchers at the U.S. Initially designed for secure military communications, it evolved into a broader tool for online anonymity, later expanding to public use with the Tor network. Another challenge of finding dark web sites is that they don’t often last long.

Sections of the dark web are often closed down too, as part of police operations. Open up Tor, and you won’t suddenly see the dark web staring back at you. Not only do you need a dark web browser, you need a dark web search engine too. This search engine will get you to the sites you need, though you can also go directly to dark web addresses if you know what they are, as with standard URLs. Tor is like the public-facing door to the dark web, and there are even mobile apps for Android and iOS.
However, if you must buy items from the dark web, set up a secure, encrypted email with CounterMail or ProtonMail. For more information, read more about the most secure email service providers in my other post. Now that you’ve completed the download, it’s time to install the Tor browser on your device. (The installation instructions that follow are for the macOS platform, I’ll mention where it’s different for Windows.) Simply double-click the downloaded file in your download folder.
So, do yourself a favor and rescale that Tor window as much as you can before proceeding. Advocacy groups are also reaping the advantages of the darknet because, here, the term of censorship is as popular as HTTPS. People mostly use it for covert communication, anonymous tips submission, and stuff like that. For instance, if you want to buy a laptop or a smartphone, you can try your luck in one of these shops.



