
The Tor network is operated by thousands of volunteers worldwide who maintain the proxy servers that protect your identity. You can download the Tor Browser for Windows, MacOS, Linux, and Android. A VPN will mask your location and stop the online breadcrumbs that can lead back to you.
The deep web includes non-indexed databases and private portals, while the dark web specifically requires Tor and includes .onion sites. This blog offers a complete guide on how to access the Dark Web using the Tor Browser, along with step-by-step instructions, security tips, legal warnings, and real-world examples. When you install a VPN, all of your activities on the dark web will be hidden from unwanted snoops from your ISP or the FBI. The VPN is a second layer of extra protection, on top of the protection that the Tor network already offers. Naval Research Laboratory mathematicians and computer scientists in the mid-1990s.
Swap Data In Countries That Censor The Internet

We’ll show you how to access and browse dark web sites, and how using a VPN to encrypt your connection can help you visit the dark web more securely. I2P is a private network built for secure, anonymous communication. Instead of the onion routing Tor uses, I2P relies on unidirectional tunnels and garlic routing, which bundles multiple messages together for better traffic obfuscation. It uses its own internal DNS to access “eepsites”, not .onion addresses. Now that you understand the essentials of anonymous networks and how to prepare yourself for secure browsing, it’s time to explore the practical steps involved in accessing the Dark Web.
Top 10 Best Dark Web Search Engines In 2025 Safe &
No matter what you do online, there’s always at least some risk of being tracked — especially on the dark web. While no method guarantees complete anonymity, you can minimize the chances of being tracked with the right precautions. As well as phishing scams, a multitude of other scams operate across the dark web. There are many fake marketplaces and platforms that might offer to sell you goods or services but actually take your money without providing anything in return. Since the dark web is unregulated, there’s almost nothing scam victims can do to seek justice or compensation. Let’s look at two popular browsers you can use to access the dark web on desktop computers and laptops.
What Is Identity And Access Management (IAM)? Benefits,
- Such sites include blogs, gaming sites, social media, and super-encrypted email platforms.
- Everything you do is protected by NordVPN, which is key to accessing the dark web and enjoying it privately.
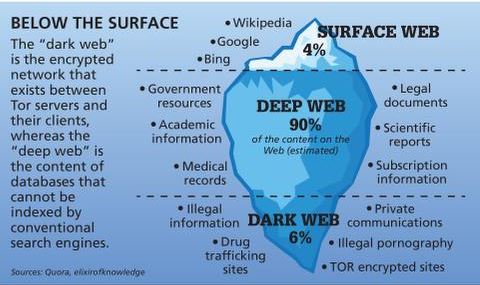
- In fact, only about 5-10% of the information on the internet is available through common browsers like Google Chrome or Mozilla Firefox, known as the ‘surface web’.
- These high levels of anonymity increase the opportunity for the “bad guys” to sell drugs, stolen IDs, credit cards, weapons, and many more compromised products or information.
- In fact, this hidden web is so large that it’s impossible to discover exactly how many pages or websites are active at any one time.
It will make your VPN activities seem like normal traffic, so you can use an uncensored internet. However, this feature is only available on iOS, Android, and Windows. For this reason, you must watch out and avoid opening anything that looks suspicious to you. Since malware lingers across the dark web, your device can easily become infected, even if you are an unsuspecting user.
Added Security: Use A VPN
Any online activity can carry breadcrumbs to your identity if someone digs far enough. On the software end, the use of Tor and other anonymized browsers is not strictly illegal. In fact, these supposed “dark web” browsers are not tethered exclusively to this portion of the internet. Many users now leverage Tor to browse both the public Internet and the deeper parts of the web privately.
The biggest and most frustrating part about dark websites is that they live for a short span of time. These platforms keep changing their addresses to avoid DDoS attacks or law enforcement agencies. In some countries, such as China and North Korea, the government uses heavy online censorship and blocks many dark web websites. This is where an Onion website, like the Tor browser, comes in handy. It is the dark web’s version of Wikipedia with a massive links directory. You will find all the necessary .onion links to access any content or service on the dark web.
Use Cryptocurrency Safely
On top of that, the installation process of Freenet is rather easy. Simply download the file, install the software, and you’re ready to use its web-based interface. In opennet mode, the network will automatically assign you to other users on Freenet’s network. As I mentioned previously, the dark web is quite popular with journalists, political bloggers and news publishers, and others who run the risk of imprisonment in countries like Iran and others. That alone might already raise suspicion and place you under special surveillance.
Best Onion Sites To Discover On The Dark Web In 2024
Your ISP (Internet Service Provider) or anyone monitoring your connection, like a network administrator, can still see you’re accessing the dark web. Some governments actively monitor dark web activity through various methods, like analyzing internet traffic patterns or using high-end surveillance software. Governments also often set up “honeypot” sites on the dark web, which mimic illegal services and wait for users to enter their info. Of course, this sort of site poses no risk to legitimate dark web users, but it’s worth knowing that your usage of the dark web in general might draw attention to you. Once you’ve securely connected to the Dark Web via Tor, the next step is locating legitimate .onion sites.
The One-click Linux App I Use For Instant Online Anonymity
- For beginners, this guide sets the foundation, and for further exploration, check out our Top Darknet Markets to dive deeper into this ecosystem.
- However, because it’s almost completely anonymous, there are a lot of illegal images, information, products, and services on the dark web.
- Some simply don’t want government agencies or even Internet Service Providers (ISPs) to know what they’re looking at online, while others have little choice.
- In opennet mode, the network will automatically assign you to other users on Freenet’s network.
- Additionally, Tor exit nodes are often blocked by websites that don’t trust them, and Tor over VPN can’t do anything about that, either.
Finally, because the dark web routes all traffic through a series of proxy servers, which are operated by thousands of volunteers around the world, the search process is typically very slow. The dark web is a tiny portion of the internet, estimated to account for less than 0.01 percent of total web content. This is because the vast majority of the internet is made up of the surface web and the deep web. Despite its relatively small size, the dark web plays an outsized role in discussions about online anonymity and cybercrime due to the high-profile illegal activities that take place there. While the surface web is vast, it only accounts for a small percentage of the internet as a whole. Everything you can search for and interact with through regular browsers is part of the surface web, but much of the internet’s data is hidden below this easily accessible layer.
When accessing the dark web, the first step is to install a dark web-friendly browser on your computer. Unlike traditional browsers, this will route your internet traffic through an anonymizing network and mask your IP address. Another great source to find and explore dark web marketplaces or other sections is to visit Reddit’s resourceful forum. You can look for information on /r/deepweb, /r/TOR, or /r/onions, of which the latter is useful to find hidden wikis and more. Many of these Reddits have rules prohibiting linking to illegal sites and services, so you likely won’t find anything illegal there. Darknet markets facilitate transactions for illegal goods and services.

The Deep Web forms a more expansive but hidden layer beyond the reach of conventional search engines. This section comprises content requiring specific permissions, login credentials, or specialized tools for access. Examples include password-protected websites, private databases, and subscription-based resources, contributing to a broader yet less visible realm on the internet. Tor is a Firefox-based browser made specifically to enable access to onion sites, hence the name The Onion Router. This browser, on paper, ensures anonymity by routing your traffic through different “secure” nodes, preventing tracking and surveillance. Later in our guide, we’ll see why this isn’t ideal for browsing the dark web safely.

In the deep net, web crawlers are blocked from accessing web pages to gather information for indexing, so the content remains hidden. Some content and services on the deep web are indexed by search engines, but paywalls or password protection prevent access. Content and services on the deep web are accessible through a regular browser. In this article, we have explored what the dark web is and how Tor Browser provides the necessary anonymity and encryption to access it. We discussed the importance of setting up Tor Browser correctly, ensuring security and anonymity, and navigating the dark web safely.
Legitimate Uses Of The Dark Web
However, while using Tor itself is not illegal, some illegal activities can occur through the network, such as the distribution of child pornography or the sale of illegal drugs. It’s important to note that engaging in illegal activities is still illegal, even through the Tor network. It is designed to provide online anonymity and privacy to its users. Journalists, activists, and individuals concerned about online privacy and security often use it. Due to its anonymity, carding, fraud, and counterfeiting businesses are thriving on the dark web. Carding refers to the theft and illegal use of credit card information, and the dark web offers a platform for criminals to sell and buy such information.



