
Speeds were stable across US, Netherlands, and Japan servers (5 free locations), which was more than enough for Tor’s already-slow routing. NordVPN runs on AES-256 and ChaCha20 encryption, has a no-logs policy independently audited by Deloitte, and offers obfuscated servers for countries that block Tor or VPN use altogether. We stress-tested it using Tor over VPN, then flipped it and ran VPN over Tor, both held up without any weird breaks or traceable info.
There’s legitimate activity on the dark web too, as activists, journalists, and whistleblowers use dark web forums for anonymous communication. These forums look similar to those found on the clear web, but the content discussed and shared by the anonymous chatters can evade censorship on public sites and surveillance. The problem is that getting to those forums may require opening yourself up to safety concerns like the ones listed above. Surfshark is a low-cost provider that ticks all the boxes for use with the dark web. It has a large network of secure servers, the ability to keep connections private, and apps that are rich in security features.
How To Access The Dark Web Safely And Securely

So, once you’ve activated your VPN and your privacy is secured, it’s time to visit Tor’s official download page. The dark web is a decentralized web, which means that the data is stored on many different servers around the world. As you are now familiar with the three different sections within the entire world wide web, let’s take a closer look at how you can access the dark web anonymously.

Stand Up For Privacy And Freedom Online

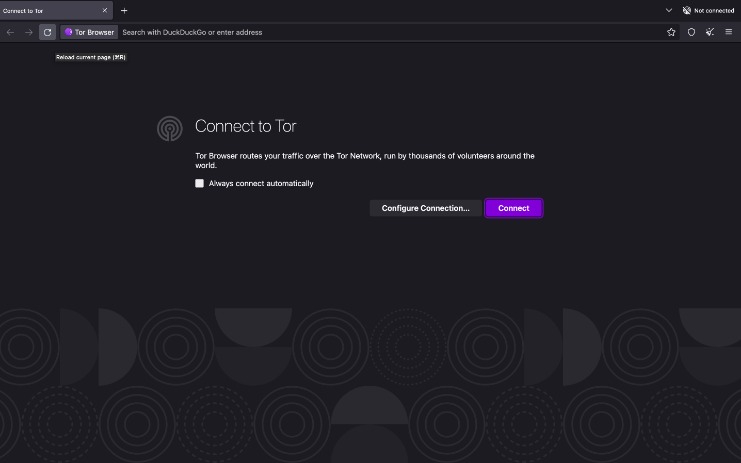
You can download the Tor browser from the official website, Torproject.org. There is no official Tor version for iOS because Apple requires all iOS browsers to use WebKit, which affects Tor’s privacy features. Initially created to protect U.S. intelligence communications, Tor was released for public use in 2003. In 2004, the Naval Research Laboratory then released the code and made it open-source. Since then, volunteers and sponsors around the globe have maintained Tor and the Tor Browser. The Onion Router (Tor) was developed in the 1990s by researchers and computer scientists at the United States Naval Research Laboratory.
How To Access The Dark Web On Your Device
Far from the widely accessible and visible surface web, the Dark Web offers a level of anonymity and privacy that attracts users seeking alternative online experiences. However, it’s important to note that the Dark Web is not without its risks and potential dangers. Illegal Products and Services The Dark Web is rife with websites offering illegal products and services. These include a wide range of narcotics, prescription drugs, counterfeit documents, stolen credit card information, hacking services, malware, and more. The anonymity provided by the Dark Web makes it an attractive platform for criminals to operate, as it reduces the risk of their identities being exposed. Digital forensics plays a critical role in dark web investigations.
Tor-Enabled OS Alternatives To Tails For Secure Dark Web Browsing
As enticing as it might be, don’t follow links to other parts of the dark web. Check around with other users and ask if they know anything about the new marketplace. Unfortunately, it’s also a place where the bad guys can offer their services – for example, hackers or hitmen. On top of that, the installation process of Freenet is rather easy.
Maintain Anonymity
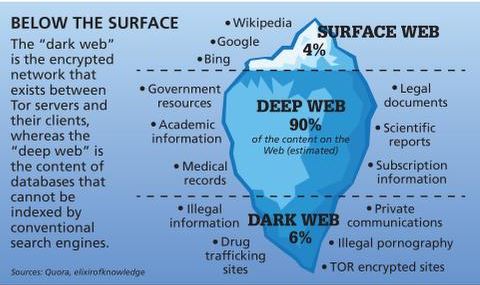
I2P, or the Invisible Internet Project, is an anonymous network layer to facilitate secure and private communication among its users. It works as a decentralized, peer-to-peer network that emphasizes censorship resistance and complete anonymity. The surface web is the open part of the internet, which includes publicly accessible websites and resources.
Use A Trusted VPN
Antimalware and antivirus protections are equally crucial to prevent malicious actors from exploiting you. The dark web is filled with information theft from malware-infected users. Attackers can use tools like keyloggers to gather your data, and they can infiltrate your system on any part of the web. Internet security software like Kaspersky Premium are comprehensive to cover both identity monitoring and antivirus defenses.
The dark web is a small portion of the deep web that has been intentionally hidden and is inaccessible through standard web browsers. To access it, you need dark web browsers like Tor, which allows users to browse anonymously by bouncing their connections through a global network of volunteer servers. The deep web is significantly larger than the surface web and includes all the content that isn’t indexed by traditional search engines. This isn’t as mysterious as it sounds; the deep web encompasses everything from your private email accounts and online banking information to subscription-only websites and academic databases. Imagine a vast, shadowy expanse of the internet where the usual search engines dare not tread — this is the dark web. It’s a hidden layer of the internet, shrouded in secrecy, that you can’t access using traditional search engines like Google or Bing.
- While Tor is the most common method for accessing the dark web, I2P and Hyphanet offer alternative options for secure and private browsing.
- Therefore, you should avoid downloading files from the dark web, as seemingly innocent files may contain malicious software.
- It aims to preserve the internet’s scientific and cultural heritage.
- It is easily accessible by the general public and requires no special configuration.
Engaging in illegal activities on the Dark Web can have serious consequences. Law enforcement agencies around the world actively monitor the Dark Web and carry out investigations to identify and apprehend individuals involved in criminal activities. If caught, individuals can face criminal charges, including drug trafficking, weapons smuggling, identity theft, and hacking offenses.
Security Links
It encrypts your traffic at the entry node and changes your IP address. This means you will get a VPN’s security and enjoy the anonymity of the Tor network simultaneously. Since the dark web is a hidden and uncontrolled part of the web, there is a high amount of malware infections present there.
How To Access The Dark Web Using The Tor Browser?
When people go on about the so-called dark web, they’re usually talking about onion sites, which aren’t searchable via Google or accessible via standard browsers. On the regular web, domains such as are translated into their actual IP addresses via the domain name system (DNS). Hide.me’s free plan gives you 10GB of data per month, which might sound small, but for most dark web sessions (especially text-based browsing), it’s more than enough.
Keep in mind that in some regions like China and Russia, it’s illegal to use anonymizers. If you’re in a restrictive country, you’ll be crossing the red line and authorities could be at your heels. The silver lining is that no one has been arrested or prosecuted for using an anonymizing browser. Cloudwards.net may earn a small commission from some purchases made through our site. Tor Browser aims to make all users look the same, making it difficult for you to be fingerprinted based on your browser and device information. Well, as long as you don’t visit sites with underaged models or that engage in human tracking or that sell drugs and other illegal items.
This search field allows you to perform regular, but now anonymized, web searches through DuckDuckGo’s Tor site. Upon opening the Tor website, you will be presented with various download options for the operating systems that Tor supports, including Windows, macOS, Linux, and Android. Carefully matching your needs to the strengths and weaknesses of each solution ensures optimal privacy, security, and usability. Formerly, Darren served on the Committee of Technology Infrastructure under Mayor Richard Daley.



