
However, the rapid evolution of these marketplaces continues to outpace many of these initiatives. In 2025, dark web markets continue to grow more sophisticated, leveraging cryptocurrency as their backbone for financial transactions. These hidden digital spaces host a variety of illegal and illicit activities, from drug trafficking and weapons sales to data breaches and financial fraud. The decentralized, pseudonymous nature of cryptocurrencies has provided a strong foundation for these underground markets to expand, adapt, and resist law enforcement pressure. Activities on dark-web marketplaces are closely monitored by international law enforcement agencies. Purchasing or selling illegal goods—such as controlled substances, counterfeit documents, or stolen data—can result in significant legal penalties, including fines, criminal charges, and imprisonment.
2 Implication Of Security Mechanisms On Data Collection
- Our analysis focuses on Bitcoin – the most popular cryptocurrency both on DWMs27,28 and in the regulated economy29,30.
- In 2024, it recorded on-chain revenue of $43.3 million, a 183 per cent increase, driven by vendor migrations post-shutdown of competitors, according to Chainalysis’ 2023 market report Darknet revenue in 2023.
- Many vendors rotate addresses and aliases regularly to avoid tracking and maintain anonymity.
- When the website returns a non-valid response, the crawler can call the Selenium component for manual interaction and inspection.
- TRM Labs noted that darknet users tend to migrate to the next “reputable” option when a marketplace falls.
As law enforcement agencies’ tactics improve, some markets respond by introducing more security features, like mandatory encryption or invite-only access. But no matter how polished or professional these sites seem, the risk of getting scammed — or tracked — is always high. Some now offer customer support, escrow systems to prevent fraud, and even user-friendly interfaces that make illegal trade feel strangely routine. Still, the dangers are severe — exposure to scams, malware, surveillance, and prosecution are just the beginning.
The cryptocurrency space remains vulnerable to scams that exploit investor trust and security weaknesses. Fraudulent ICOs, rug pulls, and phishing attacks deceive users through false promotions and impersonation tactics. These threats highlight the need for stronger security measures, regulatory oversight, and increasing user awareness. Criminals employ layering and structuring methods to conceal their illicit Bitcoin transactions, which are hard to track and regulate. By breaking large sums into smaller transfers and leveraging multiple exchanges, they evade regulatory scrutiny. These methods exploit gaps in compliance frameworks, complicating efforts to track and prevent financial crimes.

Buyers And Sellers
Escrow seems to solve the trust issue between buyers and vendors relatively well, but introduces extra security risks due to the needed trust on the market operators, which frequently exit scam. Multisig, also known as multi-signature, refers to a transaction only made after being agreed upon by two or more parties. This method is quite attractive within the dark web community because of the extra security it provides, especially when it comes to avoiding market exit scams.

Public Token Treasuries And Tokenization Are Fantastic For Crypto, But Risks Remain, Binance’s CZ Says
It’s also a marketplace for digital mercenaries; you’ll find everything from solo hackers offering their skills to well-organized groups that take on more complex or high-stakes projects. Some even have connections to criminal organizations and, in more serious cases, government-backed operations. The site gives out free samples of the stolen data every now and then to gain more customers. With its fast rise to fame and focus on money fraud, it’s no surprise that cybersecurity experts are keeping a very close eye on this one. Exodus Marketplace started to become popular after the shutdown of Genesis Market, and it replaced it successfully.

The Darknet Ecosystem Remains Highly Adaptive

Monero and Bitcoin are two of the most commonly used digital currencies on the dark web markets. However, Monero, on the other hand, is untraceable and the most trusted payment method on these markets. Therefore, most cybersecurity experts recommend using Monero while shopping on darknet markets. Still, even with these crackdowns and better defenses, dark web markets just keep coming back.
The Shift Back To Bitcoin
Due to the highly anonymous nature of the dark web market, the user registration process does not use any identifiable personal information, including the email address and phone number we commonly use on the clear web. Mnemonics are given by the market when registered and are usually a set of English words or a long, meaningless string, similar to the seed phrase one would employ to generate a Bitcoin wallet. Users need to save the mnemonic phrase in a safe place to use it to recover their account in certain situations. Users need to set up a PGP public key in the market first, and then the market will send verification information and encrypt it using that public key. MFA is often optional when browsing listings but mandatory for purchasing items. Incognito also requires users to enter their mnemonic phrase each time they log in, in addition to using PGP as MFA.
Interaction With Online Wallets

Doing so makes it harder for authorities to identify who’s behind a purchase or a listing. Vendors often build up reputations through ratings and reviews, just like sellers on mainstream platforms. To reduce scams, many markets also use escrow systems, where the site holds the buyer’s payment until they confirm the item has been delivered. In fact, there are many more aggressive security tests we could have done, such as the rate limiting and the OWASP Top Ten.Footnote 7 But for ethical reasons, we figured we did not want to be a potential attacker.
Market Operations
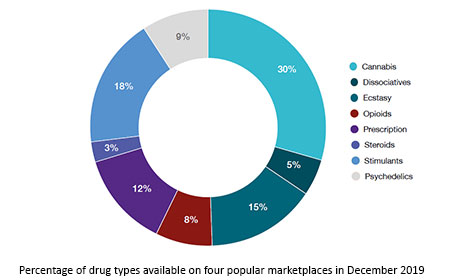
These software are also capable of launching DDoS attacks and phishing campaigns. On the dark web, you don’t need to be a technical expert to design ransomware, and that’s dangerous. Even people with little to no knowledge can buy ready-made ransomware and launch attacks on their victims. While you could find all sorts of products on Silk Road, drug sales quickly became prevalent because of the profits it raked in. In fact, by 2013, a Guardian article revealed that about 70% of listings were drug-related. If for any reason, you decide to visit these hidden corners of the web, ensure you at least study and understand the common traps.
Abacus Dark Web Drug Market Goes Offline In Suspected Exit Scam
Fraud and scam operators are also leveraging guarantee services such as Huione (discussed below), while crypto ATM scams are a growing concern, especially as they relate to elder fraud. It stands to reason that 2024’s illicit cryptocurrency volume will exceed that of 2023. Since 2020, our annual estimates of illicit activity — which include both evidentiary attributions and Chainalysis Signals data — have grown by an average of 25% between annual reporting periods. Assuming a similar growth rate between now and next year’s Crypto Crime Report, our annual totals for 2024 could surpass the $51 billion threshold. According to our metrics today, it looks like 2024 saw a drop in value received by illicit cryptocurrency addresses to a total of $40.9 billion.
However, markets with open circles do not mention any guidance about what users should do if a bug is discovered. As the most widely used security mechanism in this sector, CAPTCHAs are ubiquitous on the dark web. More recently, the privacy coin Monero has become the cryptocurrency of choice for conducting illegal transactions in the Darknet. Monero is an altcoin that was founded in 2014 and has been gaining ground because nearly all details of transactions including the digital addresses of senders and receivers, as well as transaction values, are concealed. In addition, the Coronavirus has affected postal systems around the world, meaning deliveries are not arriving on time, or in some cases at all. It is believed that big players with large operations are the majority of the markets and vendors that are still up and running.
That all is for general internet activities, you can guess how crucial having a VPN is when you hop onto something like the dark web. Then, you can set up 2FA (two-factor authentication) for that extra touch of security in case someone somehow figures out your password. If you ever have to connect to public Wi-Fi, make sure to use a VPN to keep your browsing safe and private. They’re tightening security and carefully screening anyone who wants to join. This vetting process helps keep the community “clean” from spies, law enforcement, or anyone who might pose a risk. As mentioned earlier, launching a cyberattack doesn’t require any hacking skills.
The market operators have graded the importance of different bugs, including info, low, medium, high, and critical. In terms of scope, this program covers various types of vulnerabilities, such as UI issues, server-side disclosure, sensitive data disclosure, authentication bypass, command execution, etc. There are four markets marked as half-filled circles under the “anti-phishing” column of Table 2.



