
For instance, BidenCash saw a surge in user activity following its free data leaks. If you’re unable to block the fraudulent charges, there’s no guarantee they will be refunded or removed from your statement. Resolving an unauthorized transaction involves opening a claim with your card provider, which may result in an investigation and a potentially lengthy chargeback process. We will also share some effective safety tips and discuss how virtual cards can help protect you from card fraud. Join us as we break down and discover the methodologies of card fraud using our dark web monitoring tool, Lunar.
How To Unblock Bajaj Finserv EMI Card Online
- Credit card skimmers are designed to look exactly like card readers so that people aren’t suspicious of them.
- In this article, we’ll learn how dark web credit cards work and what you can do to protect yourself from online credit card theft.
- Research by BitDefender has revealed the common prices for a range of illicit goods, from credit cards to credentials databases and more.
- As a trusted platform for money management, credit education, and identity protection, our mission is to bring Financial Power to All™.
- Ben Luthi has worked in financial planning, banking and auto finance, and writes about all aspects of money.
- – Remain cautious of vendors with no or limited feedback, as it becomes more challenging to assess their credibility and reliability.
Learn to fetch data, analyze content, and generate reports automatically. If so, this guide will help you automate supply chain risk reports using AI Chat GPT and our News API.
The scammers follow different tactics to steal credit card information. The most common ones target e-commerce websites through phishing attempts and data breaches for this purpose. Other ways include installing skimmers at ATMs and other sources of card swiping. Recent studies reveal that 63% of U.S. credit card holders have been victims of fraud, and over 50% experienced it more than once. With data breaches happening more frequently, your credit card details could already be circulating on the dark web—without your knowledge. Hundreds of millions of payment card details have been stolen from online retailers, banks and payment companies before being sold on online marketplaces such as UniCC.
The device reads the data and steals the information from the credit cards swiped at the source. No, black market websites operate illegally and pose high risks of scams, fraud, and law enforcement action. Classic darknet markets sell diverse illegal goods; data stores focus on leaked or stolen data like credentials, databases, and ID records. Launched in September 2022, Torzon Market operates on the Tor network and features over 11,600 illegal products, including drugs and hacking tools. It enhances buyer transparency by importing vendor feedback with PGP proof. Torzon offers a premium account option for additional benefits and is valued at approximately $15 million, accepting payments in Bitcoin (BTC) and Monero (XMR).
Industries That Benefit The Most From Dark Web Monitoring 2025
It tracks changes to your credit report and helps you spot potential identity theft early, so you’re not the last to know when something goes wrong. Once your personal information hits the dark web, it’s nearly impossible to remove it. But while you can’t undo a data breach, you can take control of what happens next. From strengthening your digital habits to setting up fraud alerts and monitoring your accounts, small steps can make a big difference. Skimming is the process of stealing information from credit cards using physical means. For this, the scammers install a device called ‘skimmer’ on credit card machines, like the ones used on various retail outlets.
Brief Bio: Real And Rare
While it has several legitimate uses, it is also known as the marketplace for illicit activities. Leaking credit card credentials has become a very common phenomenon on chat applications, particularly Telegram. In fact, the overwhelming majority of leaked credit cards in past months originate from Telegram channels. Carding groups and channels reach up to tens of thousands of members, as they are easy to navigate and readily accessible.
CISOs Brace For Supply Chain Attacks With Proactive Attack Surface Monitoring
N 2025, dark web websites frequently change domains and are often short-lived. Accessing them may require .onion links and the Tor browser, but caution is advised due to legality and cybersecurity risks. Apart from the dark web markets that are operating online today, some raided platforms influenced many markets. Believe it or not, some dark web marketplaces have pretty advanced systems for building trust. Sellers often need to pay a deposit to prove they’re serious, and they build their reputation through positive reviews.
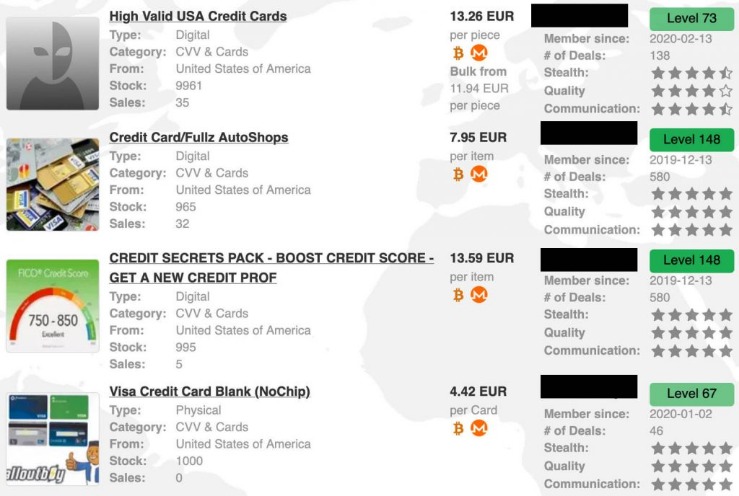
Here’s What Your Data Sells For On The Dark Web
Telegram channels supplement traditional onion sites, blurring lines between the dark web sites and more mainstream communication tools. In 2023, the dark web attracted an average of 2.7 million daily users, with Germany now leading as the country with the highest number of Tor users, surpassing the United States for the first time in years. Most of the sites i could find are related to crime, abuse and deliveries. The closures are unlikely to spell the end of darknet markets as new ones will no doubt emerge. For police, who would prefer criminals to face justice, this kind of exit causes mixed feelings. The darknet is a part of the internet only accessible through special browsing software.
Card Data And Markets

Some threat actors even run automated validation services that check card numbers before the sale, guaranteeing their buyers a certain percentage of “live” cards. This type of malware silently infect payment terminals and exfiltrate card data in real-time. The research found that the price of payment card details varied between $1 and $12 in the US, with most about $4. A fair number of vendors include access to a SOCKS5 internet proxy that can be used by the buyer to match their computer’s IP address location with that of the cardholder in order to avoid being blacklisted. The average price of a cloned, physical card is $171, or 5.75 cents per dollar of credit limit. The use of JavaScript-sniffers, also known as Magecart, has led to a significant increase in stolen payment card data.

Next, let’s explore how individuals can access the Dark Web safely, while minimizing personal risks and vulnerabilities. – Read feedback from experienced Dark Web users or trusted individuals who have had successful transactions with the vendor. Next, we will explore the significance of evaluating seller feedback and ratings on the Dark Web and how it can assist in making better purchasing decisions. As an Ex-undercover Cop, now Private Investigator, I make sure that you have the right information for the right reason under the right circumstances. With extensive knowledge using law enforcement databases and the internet, I find the information you are looking for with speed, accuracy, and the necessary discretion to achieve the desired results. Experts suggest that this giveaway serves as a marketing ploy to attract new users to B1ack’s Stash and establish its dominance in the competitive carding market.
The site also has a unique news section, listing new leaks and their size. BidenCash shop was established in April 2022, following the seizure of other card shops and carding platforms by the Russian authorities. Since its inception, it has been attracting the attention of both old and new cybercriminal customers. “Magecart is one of the most prominent criminal groups behind this activity to siphon off sensitive card data,” Mr Foss said. Cybercriminals can easily intercept your internet traffic on public WiFi without a VPN. It is recommended to use a VPN always when using a public WiFi network to ensure your online privacy and security.

The best course of action is to focus on damage control, such as cancelling the compromised card and monitoring your accounts for any unusual activity. The first step you should take is to contact your bank or credit card issuer immediately. Inform them that your card information has been compromised and discuss the best course of action, which could include canceling the compromised card and issuing a new one to prevent fraudulent transactions. Active for a decade since 2014, it is a widely used credit card shop used to source stolen credit card information such as dumps, CVVs, Wholesale Accounts. They offer scalable healthcare services that push patients towards their health and wellness goals while supporting providers’ roles to achieve those milestones.



