This often includes a “checker service,” a compromised merchant account they use to run dinky charges through to see if the card is still valid, Krebs says. If someone agrees to use the shop’s checker service instead of a third party, the shop will give a guarantee that at least a portion of the cards are usable for a certain period of time. Many tracker apps link directly to bank accounts for up-to-the-minute info. They show recent purchases, account balances, and spending trends all in one place.
As Porn Sites Apply New Age Checks, Will Users Hand Over Personal ID?
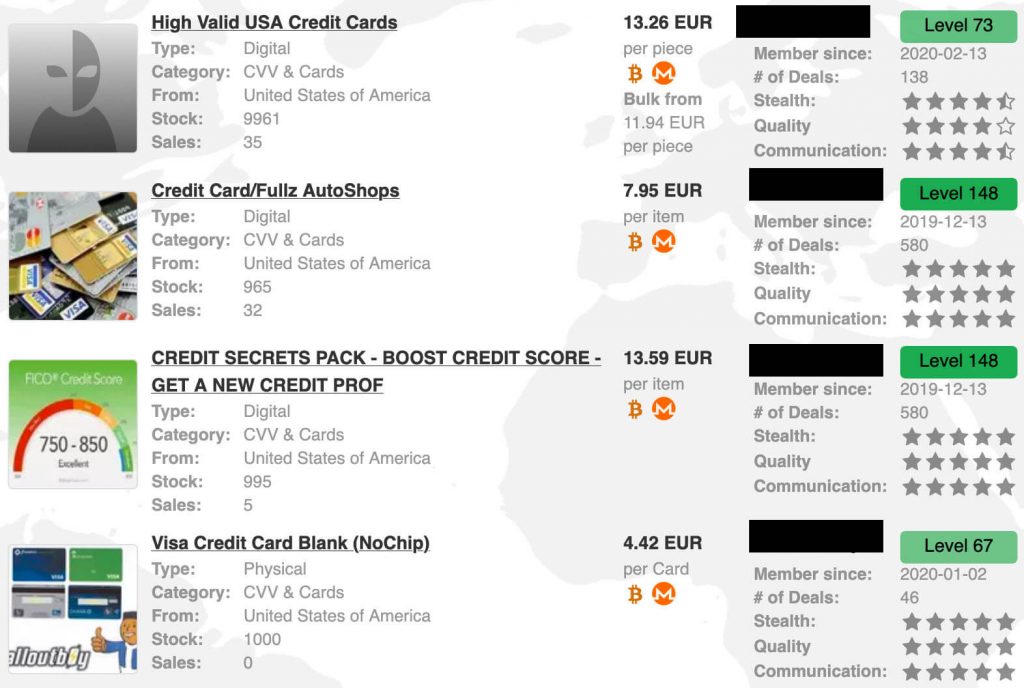
Though the vendor is still online and has blamed the issues on “technical difficulties”, it has been banned and removed from all high-profile cybercriminal forums following a major row in June. The detective started chatting with Track2 over ICQ to learn more and he found out that Track2.name was where untrusted customers go to buy stolen cards. Then once you’re trusted or you pay a $1,000 registration fee, you can then be invited to Bulba.cc, a more elite carder site.
Compromised Online Account
A 2019 data leak of another shop, BriansClub — which appears to have been by a competitor, according to Threatpost —shows how pervasive this trend has become. All content provided on Web Design Booth is for informational purposes only and does not constitute professional advice. We strive for accuracy and authority, but it is recommended to consult with qualified professionals before making decisions based on our content. Web Design Booth may receive compensation from third-party advertisers, which does not influence our editorial content. Abraham Lebsack is a seasoned writer with a keen interest in finance and insurance.
- Opt for reputable and trusted payment gateways that offer strong encryption and advanced security measures.
- A recent arrest in the Southeast Asia region marked the first time JS-sniffer operators have been caught anywhere in the world.
- Collecting used keystrokes is how hackers typically guess credit card numbers, PINs, and passwords.
- Engaging in illegal activities carries severe legal consequences and can harm individuals and financial institutions.
- Dark Web ID has been an industry leader for years because they never stop innovating to keep businesses out of credential compromise trouble.
- The globalnature of NFC payments and the anonymity provided by money mules andencrypted communication channels make these fraud operationschallenging to track and shut down.
How Do Criminals Get Credit Card Information?
Detecting and preventing dark web credit card fraud can be difficult since the dark web is, by nature, hidden. By using specialized tools cybersecurity professionals can track these illegal activities and alert financial institutions of potential threats. Dark web transactions play a key role in fund transfers for credit card fraud.
Which Wallet Best For Darknet Market

Threat actors want your passwords to facilitate everything from ransomware to spyware attacks. The latest threat intelligence analysis, however, suggests those numbers are low. Unlike carding shops, which primarily focus on the trade of information, carding forums serve a broader purpose within the cybercriminal community. On these forums, actors will often share techniques, hacking tools, strategies, and resources for conducting fraudulent activities.

How To Know If Someone Has Stolen Your Credit Or Debit Card Number
Notably, the Telegram channels offering it are named X-NFC, which may create some confusion. The actors behind the tool provide technical support and guidance on how to use it. The dark web isn’t a single destination but a collection of anonymized networks where privacy is paramount. It was originally designed to protect free speech and privacy but has also become infamous as a marketplace for everything from counterfeit documents and illegal drugs to, you guessed it, stolen financial data.
If you can, use an online wallet like Apple Pay or Google Pay, says Pascal Busnel, a director with ACA Group, a provider of risk, compliance and cyber solutions. This type of payment uses tokenization, which replaces your sensitive card data — like the expiration date and card verification value (CVV) — with a unique, random token. If the company you’re buying from doesn’t have your sensitive card information, neither will hackers that hit that merchant with a data breach. Holders of any credit cards, whether you know if they have been compromised or not, are advised to monitor bank statements for any suspicious or unusual activity. These tools scan transactions in real-time, flagging any suspicious charges instantly. Stolen financial info sold online gives scammers instant access to victims’ money.

Using Tracker Apps To Monitor Your Card Data
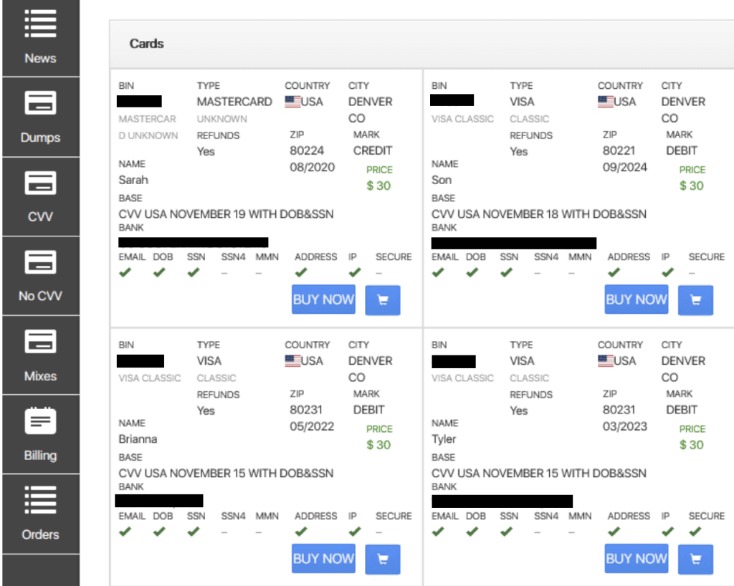
The card skimmer illegally captures the credentials of cards inserted into the machine. The stolen data is then used to create fake credit or debit cards and commit fraudulent transactions. A data breach occurs when confidential or protected information is exposed to unauthorized people or endpoints. Keeping your credit card information safe can prevent it from being published on the dark web and used for malicious purposes. If you don’t take the proper steps to secure your credit card information, you place yourself at risk of becoming a victim of identity theft which is not easy or quick to recover from. Spoofed websites are sites that have been made to look legitimate but are actually designed to steal your sensitive information.
Steps To Take If Your Credit Card Information Is On The Dark Web
His work has appeared in Time, Success, USA Today, Credit Karma, NerdWallet, Wirecutter and more. Your personal information can sell for upwards of hundreds or even thousands of dollars on the dark web—and you might not even know it’s even out there to begin with. The average price for your personal information can range from as little as $1 to more than $4,000.
How Are Credit Card Numbers Stolen Or Hacked?
Active buyers are also eligible for free gifts and dumps depending on their volume. As one of the prominent platforms supporting such activities, card shops make carrying out such scams relatively easy and popular. STYX Market focuses specifically on financial fraud, making it a go-to destination for cybercriminals engaged in this activity. It tracks changes to your credit report and helps you spot potential identity theft early, so you’re not the last to know when something goes wrong.
The illegal carding market, which can be accessed through the dark web, went live during June, 2022. Initially, this specific marketplace started out by leaking thousands of credit cards. From Social Security numbers to bank logins and medical records, cybercriminals buy and sell stolen data every day. Using stolen compromised payment data, Chinese cybercriminals automate transactions using tools like Z-NFC and NFC-enabled POS terminals, which are typically placed right in front of them. Theidentified Telegram channels provide detailed manuals on how to useZ-NFC for fraud.
The report says that Instant Relay Chat (IRC) and encrypted platforms, such as Telegram, are also providing a way for stolen data to be traded. Improve your online security by creating strong, unique passwords for your online banking and shopping accounts, using a password manager, and enabling multi-factor authentication (MFA) wherever possible. These practices will go a long way in reducing the risk of unauthorized access to your accounts. It is crucial for individuals to understand the link between credit cards and the Dark Web and take necessary precautions to protect their financial information. Understanding the Dark Web is crucial for detecting potential threats and taking necessary precautions to protect your credit card information.



