Today, many organizations exist that are created only to handle these reports anonymously and effectively. They know how to process the information and get it to the correct law enforcement agencies internationally. Since malware lingers across the dark web, your device can easily become infected, even if you are an unsuspecting user. If the above average Joe’s explanation isn’t enough for you, below are some legitimate reasons to use the Dark Web in a bit more detail. Tor anonymity comes with a cost since malicious hackers and criminals like to operate in the shadows.
Is Accessing The Dark Web Illegal?
This makes it extremely difficult to find out who you are transacting with. Also, you can set a strong password to protect your message and choose how long it will take to expire. ZeroBin is a wonderful way to share the content you get from dark web resources. It is a reliable messaging tool where you copy/paste a text or image and send it to your addressee. It aims to advance research on terminal illnesses like cancer with access to unbiased scientific publications. The website is available on the surface web and has a .onion site.

How Do I Verify An Onion Link Is Safe?
As Tor has top-class encryption by default, several dark web websites do not use this same certification. But if you are on the surface web, you should only use HTTPS sites. It’s important to note that you should always download Tor Browser from the official Tor Project website to ensure that you are getting the legitimate and safe version. Be cautious of downloading it from unofficial sources, as they may provide modified versions that could compromise your security. After completing these steps, Tor Browser will open, and you will be ready to start browsing the internet anonymously.

DOWNLOADING
When you visit dark web sites, even if you don’t have any ill intentions, you support the dark web ecosystem, which serves as a medium to conduct various illegal activities. Law enforcement agencies in many countries monitor the dark web to combat illegal activities. Cracking down on many illegal marketplaces on the dark web is the result of such monitoring. So, you risk being flagged or investigated for visiting certain sites, even without criminal intent.
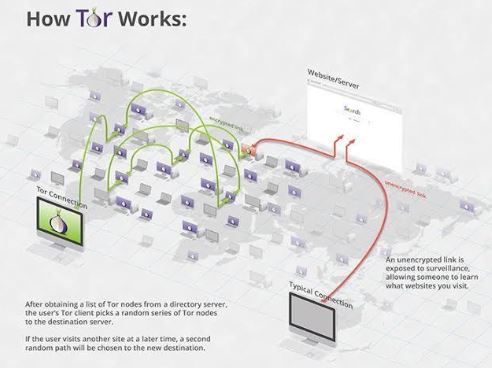
The Tor browser is mostly used to surf the dark web or evade censorship. It’s also useful if you’re a journalist, whistleblower, or activist that needs to share sensitive data with their sources, or if you’re an undercover agent. You can also use Tor to enjoy better privacy online, but I honestly think a VPN is better suited for that. The Tor browser is a web browser that lets you access the Tor network. The browser is free to download and use, and it’s also open-source, so anyone can audit the code for security vulnerabilities.
Is There A Search Engine For Onion Sites?
The dark web serves as a platform where activists can organize gatherings in secret, without the fear of giving away their plans or position to the government. Especially for these people, the dark web is the perfect platform to communicate and publish information without having to worry about imprisonment or any other form of retribution. The purpose was to protect U.S. army soldiers and agents in the field, but also politicians who held secret meetings and conversations, which contained the highest security measures. So, that means that the number of pages increased by over 100 trillion in just over three years. Hypothetically speaking, Google may be aware of well over 200 trillion individual pages (these are obviously NOT all indexed in the search engine).
Besides, LeakBase functions as a marketplace and as a discussion center where cybercriminals exchange compromised data. Moreover, it features a high number of stealer log data that includes credential pairs like passwords and email combinations. Tor was developed in the mid-1990s by United States Naval Research Laboratory employees, mathematician Paul Syverson, and computer scientists Michael G. Reed and David Goldschlag. Tor was designed to protect American intelligence communications online. Tor Browser has since become a popular tool of journalists, activists, and others that may be subject to being monitored online. If top-notch privacy is your goal, yes, you can use the Tor Browser for all of your browsing.
- Tor is used by whistleblowers who need a safe way to bring to light information about wrongdoing—information that is crucial for society to know—without sharing their identity.
- If top-notch privacy is your goal, yes, you can use the Tor Browser for all of your browsing.
- Websites you visit via Tor will see the IP address of the exit node, not your actual IP, just like websites see the IP address of your remote server when using a VPN.
- Its decentralized community structure makes it one of the best forums, and its security measures help it to withstand threats like DDoS attacks.
- The spy agency is hoping to securely and anonymously collect tips, though its entire website, including job listings, are available on the onion service.
What Is The Safest Way To Access The Dark Web?
This disables potentially dangerous features like JavaScript that could reveal your identity. NoScript and HTTPS Everywhere extensions provide additional protection against malicious scripts and unsecured connections. A reliable VPN encrypts your traffic before it enters the Tor network, preventing surveillance from your ISP or malicious actors.
The Hidden Wiki & Co

Moreover, the forums use cryptocurrencies like Bitcoin as the only mode of transactions. The digital currencies provide anonymity, and they’re hard to trace, which makes them the best option for illegal transactions. Given that these are online transactions, the parties involved want a channel that they’re sure of getting the services or goods they purchase.
Almost all dark web forum activities are illegal, and hence, the last thing users want is to reveal their real identities. Fortunately, the forums offer an option for users to operate under pseudonyms that help protect their identities. It’s the best way that users can make open communications as well as share sensitive data without exposing themselves. XSS (formerly known as DaMaGeLaB) was one of the longest-serving forums in the deep web. It was a dominant forum that featured a dangerous threat for average users within the Russian-speaking cyber environment.

It tracks Tor user activity by region, showing trends in access and adoption without collecting personal data. These insights help researchers and privacy advocates understand where Tor is most relied upon, often highlighting global patterns in censorship, surveillance, and the demand for online anonymity. Facebook’s onion mirror allows people to access it in countries that block the platform, allowing people to connect across digital borders.
Otherwise, you risk downloading fake apps that might infect your device with malware. You can now start surfing the web while connected to the Tor network. Access any site you want as you normally would on your regular browsers. Just keep in mind it might take a bit longer to connect to a site due to Tor’s slow speeds.
Commercial Services
Our article here lists good options if you want to explore such tools. Also, it provides users with an escrow service, which adds an extra layer of trust when they conduct transactions on this notorious platform. Over time, BHF has become a notable forum in the Russian cyber landscape because of its seemingly technically skilled community and an organized structure (hence, authorities aren’t able to seize it yet). There are several ways to protect your online activities from being tracked.