Today, many organizations exist that are created only to handle these reports anonymously and effectively. They know how to process the information and get it to the correct law enforcement agencies internationally. In some countries, evading government restrictions to seek new political ideologies is punishable. For example, China uses the Great Firewall to block access to Western sites. Accessing blocked content can result in being placed on a watch list or imprisonment.
Navigating Ransomware Attacks While Proactively Managing Cyber Risks
Don’t click on suspicious links, be skeptical of what you read, and avoid dark web marketplaces if you don’t want to stumble on illegal activity or content. The dark web is the part of the internet that’s not indexed by public search engines like Google. It’s made up of forums, marketplaces, and websites you can’t find with a Google search and requires specialized software to access, such as the Tor Browser. In addition, know that while accessing the dark web is legal in most countries, engaging in illegal activities (buying or selling contraband, hacking services, etc.), is illegal everywhere.
In contrast, your regular VPN encrypts your data but then connects you directly. The Guardian Project worked with the Tor Project to develop these apps, which allowed Android users access to the Tor network. However, with the release of the official stable Android Tor Browser, Orfox will be phased out and stop receiving updates. Is your internet connection acting up, or are websites failing to load properly? Tor Browser masks your IP address and routes traffic through multiple servers. If you only want to mask your IP address and don’t need to access the dark web, then going online with a VPN is much easier and faster than using Tor.
The New York Times

Hackers, journalists, and security companies use this hidden corner to exchange information and gather intelligence that’s not accessible through the regular internet. When you use it, all the web traffic automatically routes through Tor. If the operating system detects any non-anonymous connection, it blocks it, thus ensuring maximum online protection. It doesn’t use JavaScript, meaning the website won’t track your activities or exploit vulnerabilities.
What Is WPA2 (Wireless Protected Access ?
Although the Tor browser has sufficient encryption, combining it with a VPN offers better protection. However, you should not see it as an opportunity to engage in illegal activities to avoid trouble with authorities. A budget-friendly VPN service allowing users to access dark web safely anytime, anywhere, and on any number of devices they want. With rising online privacy concerns in the current digital age, the Tor network’s anonymity is becoming essential. It is a good way to prevent third parties from tracking online activities. People in countries with heavy internet censorship must get a VPN or Tor browser to access the surface web.
Https://g7ejphhubv5idbbu3hb3wawrs5adw7tkx7yjabnf65xtzztgg4hcsqqdonion/
- Users need to clearly understand these threats and proactively implement strong security practices.
- It uses the Tor network because it is a popular network that helps to circumvent censorship and online surveillance.
- The interface works smoothly, but it usually loads slower due to Tor routing.
- Because of the relaying of data through the onion nodes, and the encrypting and decrypting taking place at each node, your internet connection will slow considerably.
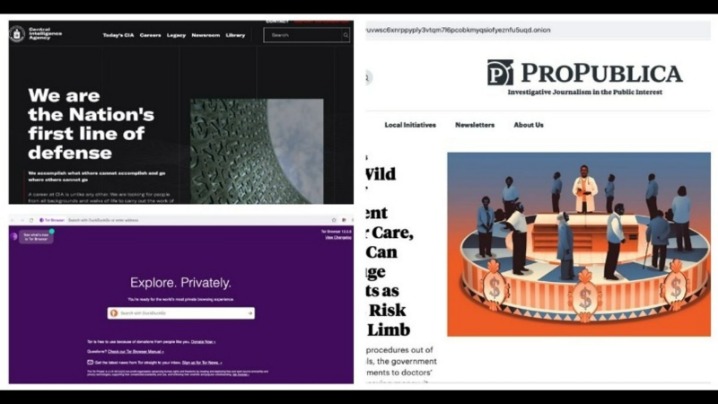
However, technological advancements such as encryption and privacy-focused browsers like Tor enabled the general public to access it. While it might appear tempting to venture into the dark web, it’s crucial to understand that the risks here are far more severe compared to the deep web. Therefore, if you do decide to explore it, exercise extreme caution. No one is hiding here—they’re just guaranteeing that people in censored countries can read the news without being flagged. As listed above in our article, even respected organizations like the BBC and ProPublica have a version of their site on the dark web.
Can You Use The Tor Browser On A Mobile Device?
Hidden networks also host a range of resources that can inform, educate, and support individuals who value anonymity. From uncensored libraries to secure whistleblowing channels, these platforms can offer benefits difficult to find on the clear web. Dark web websites look pretty much like any other site, but there are important differences. That’s “a special-use top level domain suffix designating an anonymous hidden service reachable via the Tor network,” according to Wikipedia. Browsers with the appropriate proxy can reach these sites, but others can’t.
(The installation instructions that follow are for the macOS platform, I’ll mention where it’s different for Windows.) Simply double-click the downloaded file in your download folder. Then, simply click the operating system that you are using and download the file. While an iOS version of the official Tor browser is not available, there are Tor-compatible browsers available in the App Store. So, once you’ve activated your VPN and your privacy is secured, it’s time to visit Tor’s official download page.

Verified Social Channels And News Sites
Your download and upload speeds may be slower, but that is the tradeoff for secure Internet browsing. To access the dark net and Tor using Brave, open the browser, choose the hamburger icon from the top toolbar, and select Private window with Tor. You will be connected to the Tor network, and then you can open onion websites and obfuscate your network activity.
The dark web, with its complex layers and concealed corners, is a fascinating yet formidable part of the internet. By approaching it with caution and equipping yourself with the right tools, such as Forest VPN, you can explore its depths safely. Whether you’re seeking out information, participating in political discourse, or simply curious, the dark web can offer a unique digital experience that respects your privacy and security. Discover how to navigate dark web websites app safely with tips for privacy and security.
That means the ability to have all activity completely auditable to ensure the safety of the company and analysts alike. It also means the ability o manage attribution so angry site admins don’t track a researcher back to their real-life persona, and protection from easy-to-click malware. A cloud-based isolated browser, such as Silo for Research, is needed to allow you full access with an easy-to-use service that works in sync with your company’s IT security and compliance. By diverting traffic through multiple nodes on its way to the client, the originator of files and sites can be hidden, making them more difficult to trace. You can conduct discussions about current events anonymously on Intel Exchange.
Tails never writes anything to the computer’s hard drive, running only from the RAM of the computer, which is wiped clean when the computer is shut down. However, there are several “.onion” search engines like “onion.city”, “onion.to”, and “notevil” that you can use to find suitable marketplaces. The “Hidden Wiki” (which can be accessed in a normal browser) offers a large collection of dark web links, but be careful, as many of those links are to dangerous websites. Naval Research Laboratory mathematicians and computer scientists in the mid-1990s. The U.S. Army developed “onion routing” to protect intelligence communications online. Unlike the surface and deep web, you can’t access the dark web via a standard or specialized search engine.
- Since activists, journalists, and advocates need the dark web to communicate securely, find evidence, and bypass censorship, it remains a tool for privacy and free expression.
- The best thing is to actually understand how to find the fresh, new links.
- Tor blocks JavaScript by default, but this addon lets you permit it for trusted sites.
- Nevertheless, due to IP masking, users may appear to connect from a different location, potentially leading to some sites attempting to block Tor users, limiting access.
- In 2008, the first Tor Browser was released, making it easier for any internet users to access the dark web.
- Moreover, this shop provides detailed statistics about each user profile on the platform, giving users a better idea about the vendors for the buyers and vice versa.
Especially for these people, the dark web is the perfect platform to communicate and publish information without having to worry about imprisonment or any other form of retribution. The purpose was to protect U.S. army soldiers and agents in the field, but also politicians who held secret meetings and conversations, which contained the highest security measures. The dark web addresses are a randomly-scrambled sequence that generates URLs, mostly hard to remember ones. For example, the URL of Silk Road is rather unintelligible and may look something like “gan4arvj452janndj4a76.onion”. It’s the last part of an internet domain name, stated after the last dot.
The best part is that with Orbot, you can block or unblock specific apps. However, the app says it works best with social media and messenger apps. And, of course, you can connect to any Onion sites right on your mobile device. With a network of Tor bridges, you can remain online even if the network is restrictive. Once installed, it makes your entire mobile network go through a VPN.