On top of that, the installation process of Freenet is rather easy. Simply download the file, install the software, and you’re ready to use its web-based interface. The advantages of I2P are based on a much faster and more reliable network.
Safely Browse And Verify Onion Sites
This makes it more difficult for authorities to locate and take down these sites. That’s why they’re often a popular means of communication among activists, whistleblowers, political organizers, and ethical hackers. Of course, cybercriminals can also use them for nefarious purposes like discussing illegally shared interests, conspiring to commit crimes, or posting content deemed too unsavory for the clear web.
How Much Does It Cost To Use Tor Browser?
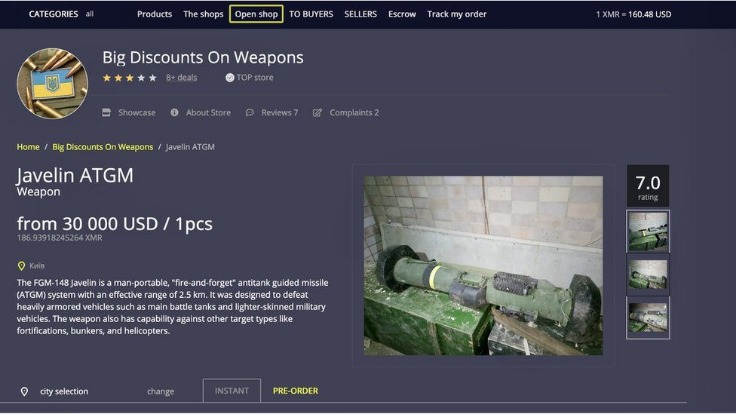
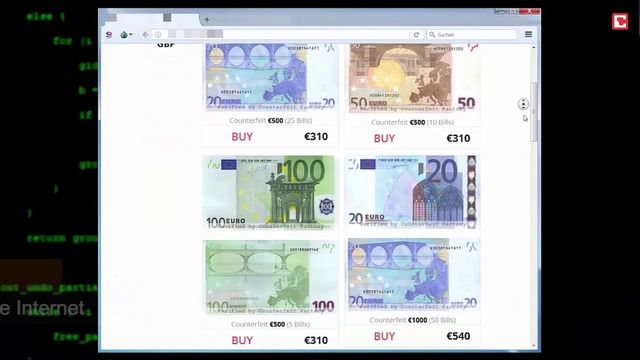
The marketplace supports multiple payment methods, including Bitcoin (BTC), Litecoin (LTC), and Cryptocheck. They add new batches of stolen data every other week, and there’s even a bidding system where buyers can place offers on new data batches as soon as they become available. Now that you understand what the dark web is all about, you might wonder why other people do things on it. Darknet marketplaces like to exist on the dark web because it offers a service that the regular internet, or more accurately, the “surface web,” does not. Although these marketplaces are continuously shut down by law enforcement agencies, they still work today.

However, remaining anonymous can be invaluable to protesters, civil rights groups, journalists, lawyers, and other vulnerable groups. Illegal marketplaces are merely a small fraction of what’s actually there. Our editors thoroughly review and fact-check every article to ensure that our content meets the highest standards. If we have made an error or published misleading information, we will correct or clarify the article.
Is Accessing The Dark Web Illegal?
With this setup, you connect to your VPN first, then open Tor Browser. That means your ISP only sees encrypted VPN traffic and can’t tell you’re using Tor. It also hides your real IP address from Tor’s entry node, which is the first hop in the Tor circuit. Avoid fraudulent Tor-like browsers that compromise your online security.
Standard Chartered’s Alvaro Garrido On AI Threats And What CIOs/CISOs Must Know In Their AI Journey
If the above average Joe’s explanation isn’t enough for you, below are some legitimate reasons to use the Dark Web in a bit more detail. The use of the dark web raises suspicion as it shows there is something you want to do privately. Remember that illegal activities can still incriminate you, whether you are using a Tor browser. For example, you shouldn’t pirate copyrighted material, engage in terrorism, or share illegal pornography.
How Complex Are Dark Web Marketplaces Currently?
All your traffic is automatically routed through the Tor Network. Ensure you download the Tor Browser from the official website to avoid downloading malware, spyware, or other viruses to your device. The dark web, or dark net, is a small part of the deep web that is kept hidden on purpose.
Essential Safety Tips To Minimize Risks
It blocks trackers, prevents user fingerprinting, encrypts data, and reroutes your browsing so no one can see where in the world you are. Use VPN, avoid logging into personal accounts, enable Tor security settings, and stick to trusted sites. Tor anonymizes by bouncing traffic through relays; VPN encrypts and routes through a single server. Secure communication for journalists, accessing privacy-focused forums, and whistleblower submissions.
However, technological advancements such as encryption and privacy-focused browsers like Tor enabled the general public to access it. Some markets even sell privacy tools, but you are more likely to run across counterfeit prescription pills and stolen identities. Some markets are relatively short-lived (thanks to law enforcement), but others are notorious enough that they survive, for instance, Silk Road, AlphaBay, and Hansa. The dark web isn’t just one sketchy marketplace hiding in a corner of the internet; it’s more like a messy, unregulated community with everything from freedom fighters to full-blown cybercriminals. One option is to try DuckDuckGo’s .onion version, which is great for privacy.
- There are many legitimate uses for dark web services and communication.
- This helps support our work, but does not affect what we cover or how, and it does not affect the price you pay.
- Their URLs (aka dark web links) have .onion as the domain, instead of the common surface web domains like .com or .net.
- Bear in mind too that laws about freedom of speech and censorship vary from country to country, which is part of the reason the dark web exists in the first place.
- NordVPN and many other providers offer Tor Over VPN or Onion Over VPN – whatever you want to call it.
Cybercriminals on the dark web marketplace always look for new victims to target them with scams or infect their devices with malware, spyware, or adware. Thus, use the best antivirus software that protects against these online threats. The Silk Road was a famous dark web marketplace where users could buy and sell goods and services anonymously. All the payments were made through cryptocurrency, further enhancing marketplace anonymity.
- You may also use it to access the regular internet more anonymously.
- As the most widely used anonymity network, Tor routes your internet traffic through a series of volunteer-run servers (relays) around the world.
- Early participants may see some profit, but that money usually comes from new victims, not actual earnings.
- Keybase is an exciting identity service that aims to make it easy for you to link the presence of your online identities together in a cryptographic way.
- On top of that, the provider offers perfect forward secrecy (PFS).
It’s important to note that although the dark web has many valuable services, it is also a hangout for cybercriminals. Overall, Subgraph OS is a secure and privacy-focused operating system well-suited for high-risk environments. Additionally, you can opt for Subgraph OS as a second option to Tor. The early version of Tor was created to mask spy communications.
While accessing the dark web isn’t necessarily wrong or illegal, it’s important to know how to navigate this part of the internet safely. Accessing the dark web isn’t like surfing the web everywhere else online. To access a dark web resource, you will need to know its web address to the letter. These websites will also use .onion top-level domain names, and many of them will be very long, random combinations of letters and numbers. You won’t be able to access .onion addresses using a standard search engine as they aren’t indexed by crawlers.
For many people, the answer is by using regular websites such as Reddit. The moderators enforce a strict policy against posting links to illegal products or services, so you’re more likely to find safer dark web addresses here. Tor is both a type of connection – with the extended relays – and a browser. With your device running a Tor browser, you can go to Tor-specific sites – those with an .onion suffix — or also visit the usual sites on the open web. The connection between Tor’s dark net and the regular internet is bridged via an ‘exit node’.



